The new variant of MBRLocker (a.k.a DexLocker) ransomware has a few interesting tricks to be more stealthy with researchers and more punitive with those trying to crack the unlocking password.
Malware to boot
MBRLocker is a ransomware that aims for the Master Boot Record part (MBR) of your computer’s hard drive. The MBR stores the information needed to start Windows and this malware replaces it with a malicious BIOS program which asks for a ransom before allowing Windows to start. It was first seen in the wild about a year ago.
MBRLocker ransomware has a strong psychological impact on its victims, since they can’t even boot their systems into a safe mode. However, with the aid of an extra bootable device, it is much simpler to unlock than traditional ransomware.
Two-step changeover
The enhanced stealthiness is achieved with two changes. First, the malicious payload is triggered only when a user closes the Trojanized application’s main window (another anti-sandbox trick). Secondly, it does not reboot the system immediately. MBRLocker also penalizes victims that try (unsuccessfully) to guess the password. The victim able to partially recover just the first three characters of the password is rewarded by getting back a broken MBR (with an encrypted primary partition table).
Steps to MBRLocker
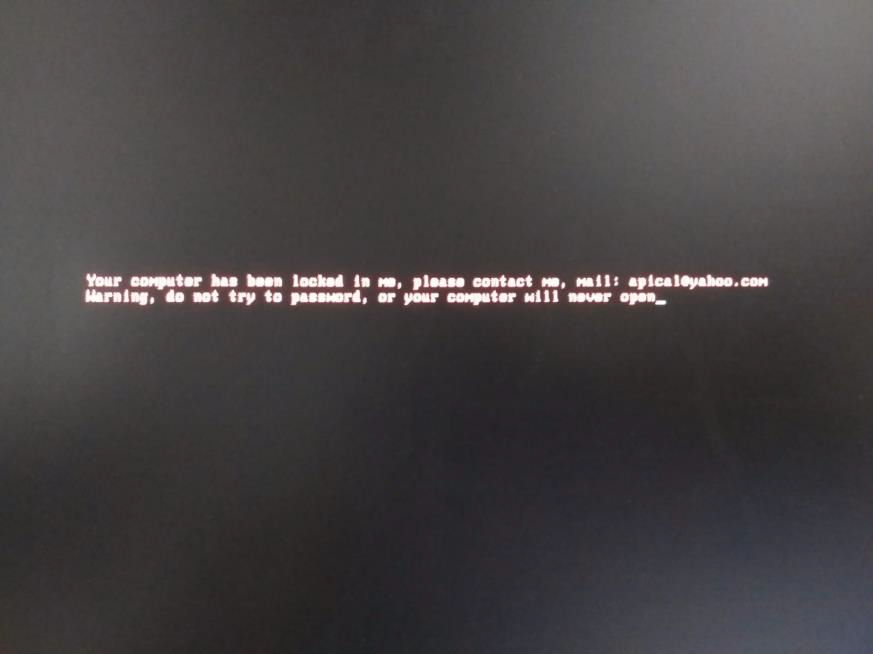
The actions taken by this ransomware are summarized as follows:
- First the content of the MBR is read and the last part of it (the primary partition table) is XORed with a single byte key
- The resulting buffer is copied to the third sector of the hard drive
- The MBR is overwritten with a small BIOS program which:
- Displays the ransom message (see screenshot) using the BIOS interrupt 10h
- Gets keyboard input using bios interrupt 16h and stores it in memory until enter is pressed
- It then scans the input buffer for a match with ‘WWe’
- If there is a match, then the first character after it is placed in a global variable
- The contents of the third sector are read in memory and the last part of the resulting buffer (encrypted primary partition table) is XORed back with the global variable
- The MBR is overwritten with the resulting buffer. (If a wrong character is entered after‘WWe’, the victim will end up with a broken MBR)
A password cracking PoC video has been published on YouTube that can be used as a guide to recovering candidate passwords. This might help already infected users:
https://www.youtube.com/watch?v=2esR5UKU3DQ
At the time of this writing, Avira was one of the few AV vendors which successfully detected this threat
(TR/MBRLocker.A).
IoC
54eec790eae50670367e30f7f21c722cf7afaafaeff00beb0b65d33517515b30