Avira Threat Protection Labs team have uncovered a rise in vishing and smishing attacks. These attacks are a serious threat not only to devices, but to the person behind the data.
Discover how job seekers are being targeted, as evidenced by the Avira team engaging with a range of scammers. Sharing a resume containing personal information is no longer enough, scammers request additional information and even funds to secure a job. This great vulnerability could lead to the victim being targeted by ransom emails, as well as their identifying information being shared or sold on the dark web.
The results serve as a timely reminder of the need for comprehensive device security, combined with strong vigilance. Mobile device protection and security mechanisms can help identify phishing attempts, flag compromised links and scam messages and even identify spoofed caller IDs, but by the nature of the tactics used, these attackers are preying on people’s need for a job, refund, or fears, to willingly give away their data and even control of their devices.
The Avira team share here how they engaged with a few of the cybercriminals who recently reached out via SMS or other similar types of mobile text – highlighting just how convincing their approaches may or may not be. The advice is to check at every stage the authenticity of calls, messages and emails, cross-referencing against legitimate websites, checking URLs and avoiding giving affirmative answers to cold callers or automated messages.
The Approach
Interestingly, the Avira Threat Protection Labs team is observing a strengthened link between phishing, smishing and vishing attacks. If you’re unfamiliar with smishing and vishing, these are targeted approaches to unsuspecting victims, duping them to compromise data, corporate account information, or to providing remote access to devices and servers, so they can steal confidential information.
Attackers are now using secure sensitive information first leaked through email phishing, or SMS (called smishing), for vishing – where the attacker impersonates someone, an official or position of authority, to steal confidential information. A hack or a social media takeover for example, may use vishing as a technique to gain access to a corporate network, while spoofing may lure the victim in, as they willingly share sensitive access information, data, passwords and log in details.
Attackers are also re-using the same email phishing or smishing “script”, to conduct vishing attacks, even using an irrelevant subject, as they go from their initial email phishing or smishing attack.
Note: These are real samples found in the wild, we did not generate them and any logos or trademarks displayed are the registered trademarks of the respective brands.
WhatsApp and the WhatsApp logo are the registered trademark of WhatsApp LLC.
Siemens and the Siemens logo are registered trademarks of Siemens Trademark GmbH & Co. KG.
You’ve won the jackpot!
Smishing is a way of tricking a person by means of Short Message Service (SMS). Cybercriminals want to reach people at source, so they’re now extending beyond mobile service providers and using services such as WhatsApp, Telegram, Instagram and Facebook Messenger to reach their audience.
Typically the text requires the victim to take an action, clicking on a link which could range from a topic like winning the jackpot, a delivery message or a prize to be claimed. Subjects could also include an urgent need for Covid testing, a financial issue or now more commonly, a career opportunity. The world is more aware of scams, making it a tougher sell for these cybercriminals, as people are less likely to click on links in these messages or visit the websites, so the less savvy attackers are dealing with a tougher crowd.
If you’ve received an unexpected message, check it carefully for the following:
- Grammatical mistakes
- Numbers in place of letters (‘O’ replaced by ‘0’)
- Sender as an “Unknown contact”
- A reference to money or a free prize
- If it generates a need for urgency
As an example, below is a fairly typical SMS targeting job seekers, with key indicators from the outset identifying it as a phishing attempt.
- The body of the text purports to come from a HR department recruiting for a specific role – while killing English grammar as much as possible.
- While such an unexpected message has red flags, the key disconnect is the sign-off as “Principal” – also suggesting that this campaign may have been used to target parents previously, potentially relating to online classes.
- Also worth noting, is the letter ‘o’ in home and job are replaced by ‘0’(zero).
- This burner contact in the link “hxxps://wa.me/919786369987”, the short URL, is short for “WhatsApp me” – redirecting the victim to a WhatsApp account to persuade the victim to give away personal details, as a secure way of communicating.
Engaging with a Scammer
The Avira Threat Protection Labs decided to engage with a scammer targeting job hunters, via WhatsApp. This vishing attack is the result of the scammer using phone numbers collected by previous phishing attacks, potentially accessed via a breach and available on the dark web.

This WhatsApp message states that this is the General Manager of an electronic and tech retailer, offering an easy income. This scam includes a WhatsApp link.
Prabhakaran Ravichandhiran from the Avira Protection Threat Labs, engaged with the texter to establish if any new techniques were being deployed for this scam. As part of that interaction, Prabhakaran intentionally matched the scammer’s grammar to suggest he would be a comparatively easy victim to scam. He also avoided giving affirmation replies, such as Yes or OK, to judge the scammer’s reaction.
With no knowledge that he was dealing with a Cyber Safety expert from Avira, the scammer pushes the potential victim to create an account on his or her website. Using this tactic, a real jobseeker would have no option but to click on the link and register their email and a password. To register, the website required an invitation code, giving the ruse a sense of professionalism.


Registration page & Login Page
It didn’t end there, the scammer asks to connect using Telegram, rather than continuing with WhatsApp. There are potentially a range of reasons for this. Telegram offers a high degree of anonymity, it includes a ‘secret chat’ option and it’s easy to pull data from it. It can be used as a command and control server to take over devices, so there is the potential for a cybercriminal to access their victim’s device.
The Avira team continued to engage by connecting with the scammer on Telegram. This particular career opportunity took a twist, as the scammer insists that username and contact details are shared – potential victims might begin to get suspicious at this point, but we obligingly send a screenshot of our registration.
That’s when it gets interesting, as we receive the scammer’s confirmation of our registration. We are then informed that the scammer has applied for a part-time job on our behalf. This is where the scammer tries the next move, stating that the job requires that we transfer funds into our account on his or her website. This is unlike any previous job search we’ve experienced, and we would question how many job seekers would fall for this, having already jumped through a number of questionable hoops.

We don’t jump right away. After being asked for payment we delay the conversation for a few minutes. There’s a swift follow up – asking if we have queries and a kind offer of guidance.
Not wishing to reward this scammer, we capture screenshots and play for time. The scammer begins to get anxious about the delay, not satisfied to hear there’s been a glitch with registration and password. The cybercriminal is losing patience, repeatedly asking for screenshot.
We left him or her languishing, leaving the conversation and swiftly changing all the details provided, blocking their contact and reporting their account as spam. Let’s hope our wasting his or her time helped prevent others being targeted during the time of our interaction.
You can read through the entire exchange, across both WhatsApp and Telegram, below:
Conversation via WhatsApp:
Conversation via Telegram:


Phishing attack – Job Advertisements
The Avira team engaged with a scammer using a different approach to target those looking for a career change or new opportunity. This tactic is a globally observed phenomenon, with scammers using legitimate company names, logos and spoofing phone numbers, hiding behind legitimate job portals where they can then download your resume by copying real job advertisements.
This scam gives cybercriminals access to email data, the job seeker’s email ID and contact information, even physical address and employer’s details. They could then sell this information or use that newly acquired data to scam their contacts further, or even threaten them with ransom emails. The victims themselves may also forward these kinds of emails to their circle, who may also lose personal information. The advice here, is always check on the actual company website careers page for the original advertisement and apply through their website.

We’re detailing one fairly typical example here, which has been designed to convince the victim that they have a job offer.
A check of the email address would flag that the email is from a domain named as “easysarkariexam”, not the company they wish to suggest they are recruiting from.
In the subject it is clearly visible that “CO” as in COnfirm is in uppercase and the Apply button is misspelled – legitimate and well-recognized companies don’t make these mistakes in their emails.
We played along and established that once the victim clicks the “apply” button, or on the job profile or logo, the victim is taken to “hxxps://www.inboxjobs.in/final_company_new.php?id=6”.
Here there is a description of the company (as per the logo), which immediately suggests to the victim that this is legitimate, further encouraging them to click to the next page.
When the user clicks on ‘Next’, the URL remains the same and the content is dynamically generated. It includes the requirements needed for the job and technologies used, as part of attacker’s deception.
When the submit button is clicked, the page is again refreshed with vague contents detailing job responsibilities. Then the victim is encouraged to click on ‘Submit’, for some important details to be revealed.
This is the step where the attacker plays his trick, forcing the victim to give away his personal details by submitting their desired salary.
They are then redirected to the actual job portal of the company where the actual Job description and details are posted.
The case where our data is sent to multiple domains is confirmed while trying to unsubscribe from the email, as our email id is in their mailing list.
When trying to unsubscribe, the request was to send to “hxxp://easysarkariexam.com/unsub1.php?email=<email id>” but also the URL was redirected to “hxxp://www.jobseeka.in/Unsubscribe.php/?email=<email id>”.
Vishing Attack
Even conference call systems may be used for vishing attacks. Typically back-to-back calls arrive from unknown numbers and unknown locations, as the attempt is made to connect with the victim and initiate their ploy to give away confidential information.
Regardless of how you are contacted, there are simple steps you can take to avoid being scammed.
- Stay vigilant and informed on the latest scamming campaigns, there are informative Avira blogs with tips and advice.
- Avoid giving away personal information to unknown person and unknown emails. Check the origin of any communication and verify the sender of the email, call or text message – and confirm it every time, before divulging any personal information.
- Avoid giving single word answers or affirmative responses directly to the questions asked from an unknown person/number. Answering “yes” to a question could allow them clip the voice with a click to a different question, to get the personal/confidential information.
- Eliciting yes answers has also been used with scams offering something that is ‘too good to be true” – an awesome subscription for a small price, an exciting loan with the lowest interest rate on the market, with a question asking if the victim may benefit from a personal loan.
- Watch out for questions designed to elicit your name, “Am I speaking with Mr/ Mrs <question>?” and then seeking to verifying the phone and SIM are registered in that name.
- Germans have been targeted by scammers using local German numbers, including an automated call which claims to be: “from Europol, to indicate that your German Identity number was used in fraudulent activity. For more information press 1”. Europol has addressed this vishing attempt on its website, stating: “Always be suspicious of alleged calls from police officers, the judiciary or bank employees. Never give out data and never give money or valuables to strangers”.
About the Avira Threat Protection Labs
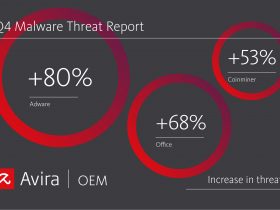
Avira Threat Protection Labs is observing a significant change of shift in using new attack vectors, with mobile text messages increasingly being used for smishing and vishing.
Avira Threat Protection Labs consistently tracks new and innovative cyberattack trends and offers advanced security features in our solutions, designed to help secure devices and data.
The Avira Threat Protection Labs team is a dedicated team, with team members based around the world, which also has its own research arm – this research arm focuses on emerging and developing cyberthreats. Avira Threat Protection Lab is the heart of the cyberthreat detection and protection unit from Avira. The researchers at work in the Labs are some of the most qualified and skilled anti-malware researchers in the cybersecurity industry. They conduct highly advance research to provide detection and protection to millions of people world-wide.