It’s tough to decide whether an app is a nasty example of stalkerware — reporting on what, where, and when the tracked individual is doing something — or a legitimate tracker like a parental control app for a child’s phone. Both stalker and parental control apps have many of the exact same functionalities of listening, restricting, and tracking. They might even be marketed by the same people. The question becomes: Is the tracking app helping a parent keep their child on the straight and narrow path home from school, or is it being used to control and eavesdrop on a significant other’s every move and social interaction?
How to determine if an app is stalkerware
Tracking apps such as spyware, stalkerware, and parental control apps all fall under the same operational umbrella as they contain a bundle of similar functions. The reason it is hard to discern between stalkerware and a tracking parental control app is that the technical makeup of the two is almost identical (but there are some suspect variations). The primary difference is in how they are used and the intent of the person installing them. In terms of parenting and with IT, judging the intent becomes a matter of perspective.
Spyware is usually seen as a malicious app, due to its invasive functions in the hands of cybercriminals and law enforcement. The most famous example of spyware is Pegasus, developed by the Israeli NSO Group and has been linked to spying on the activities of everyone from Mexican journalists and Saudi activists. Spyware such as Pegasus have an incredibly extensive range of snooping and installation capabilities and it can be installed by the victim by simply answering a call.
Stalkerware is usually pitched as the perfect app for anyone to secretly install and spy on the online activities of those close to them. Stalkerware apps have more spying and controlling features than the parental apps. Some of these functions include phone call recording, data extraction, assuring persistence and reconnaissance, location history, remote microphone/camera spying, activity monitoring, conversation eavesdropping, access to social media and storage media contents, unauthorized access, keylogger, and more.
Parental control software is a kinder and more gentle version that is marketed as a way to have more control over the safety of one’s children. Typical parental control apps have main functions like allowing parents to read their children’s text messages, know about their location by tracking via GPS, and monitor children’s browsing and search history. Moreover, some parental control apps have more serious surveillance capabilities like collecting information from social media accounts, accessing private contents of someone’s phone, for example, photos and videos, enabling remote unauthorized access, turning on and off the device remotely, and keyloggers.
Discover free spyware protection & removal
Stop intruders from stealing your confidential data.
Are spy apps legal?
As you can see, many of these tracking apps have overlapping functionalities and because of this, they are often considered dual-use apps. This means that the same app can be used for several purposes – including those that are non-legitimate. However, what is clear about whether you are using a spyware app or not is whether or not you have consent from who you want to track. Stalkerware is almost always installed on the device without user’s knowledge and consent. Here’s a quick set of questions to test if you are using stalkerware or a legit tracking app.
1. Is the tracker app on my device?
A: Yes, I know about it and willingly accept this – OK (It’s a company phone)
B: I don’t know. – Not OK, this is bad
2. Did I put the app on someone else’s device?
A: They know and willingly accept this – OK (parental guidance app)
B: They don’t know – but I have legal approval to do this (questionable).
C: They don’t know. – Not OK, this is bad.
Knowing is a critical part of the distinction. Legitimate apps display their monitoring activities to the user and the illegitimate apps generally hide. If the app is secretly installed or concealed, it is almost certainly stalkerware and is careening into legal and moral difficulties. Yes, there are exceptions to this – like with a tracking app is installed to collect evidence of a crime, but the general principle holds.
Tracking apps that the device holder knows about – like the work computer that this article is being written on — is generally OK if it is announced, tracking is in line with business activities, and there is limited private info recorded. Secretly tracking what a person is doing and their online activities is OK if legally approved. But that still leaves a wide range of tracking software available to the average person that could be an illegal invasion on another’s privacy. Similarly, parental control apps marketed for the purpose of tracking and controlling children activities with hidden monitoring functionalities can have serious repercussions on childrens’ private lives.
Device security issues with parental control and stalkerware apps
The most visible division between acceptable and monitoring software is in the icon on the device monitor. Most – but not all – parental control apps usually have icon which is both clearly visible and which also accurately describes the app function. Malicious and invasive stalkerware will usually have invisible or deceptive icon to hide the real functionality.
An acceptable parental control app will usually have limits over what apps are allowed to be installed on the device, control capabilities over screen time, and records on the browser history (there is a difference between controlling and monitoring). Unacceptable tracking apps step over the line when they enable monitoring or access to private data such as conversations. It is also a problem when there is no visible installation or app icon. While children often do need some guidelines when it comes to app use, it should be noted that many security and anti-theft apps for smartphones already come with a bundle of remote geo-tracking options.
Tracking and control apps are not security neutral. First, they essentially open up a back door to the device that, when fully exploited, can let a hacker have various levels of access and privilege. That can include authentication bypass, executing malicious code and remote commands, data theft, modification of user files, and sniffing out network traffic. Second, the data taken from the device can go to an unsecured location where it could be leaked. For example, Family Orbit, a parental monitoring company, stored files in unsecured cloud storage sites which resulted in the leak of private data such as email addresses, devices ids and names, credentials, and media storage files.
Spyware is considered malware
Security companies that have usually focused on detecting malware, direct threats to devices, and privacy are waking up to the risks to their users from tracking apps. Increasingly, invasive tracking apps are being directly identified as malware. Others such as Employee Work Spy and Mobile Tracking have been removed from the official app stores. Commercial spywares are now often detected as stalkerware and classified as PUA – a potentially unwanted app with the detection identification of PUA/Stalk. This PUA ranking recognizes that there are legitimate tracking apps (parental control) with legitimate functionalities while acknowledging the end user has the right to know what is installed on their device and its activities.
Analysis of PUA/Stalk.FlexiSpy
FlexiSpy is one of the more famous stalkerware applications. Although FlexiSpy positions itself as parental control tool with specific app features like geo- tracking and application activity monitoring. It also includes a long list of other features that can give the device administrator full access to the controlled device. Spy functionalities include call recording, taking photos and recording videos from device cameras, getting private information from chat applications (Skype, Viber, WhatsApp and others), keylogging, password extraction, remote control via SMS text commands, and more. Besides this, FlexiSpy tries to hide its presence and activity on the devices. It does this by hiding the app icon, deleting itself from any app lists, and even masquerading its presence under a random name. We’ve highlighted below some of the spying and controlling features of this stalkerware other than those which are mentioned above. Avira detects this app as PUA/Stalk.FlexiSpy.
Hide or Enable/Disable Application icon
The below images show FlexiSpy installed as Android Sync and Sync Services. It shows that the application is trying to show that it is some kind of Android OS related tool.



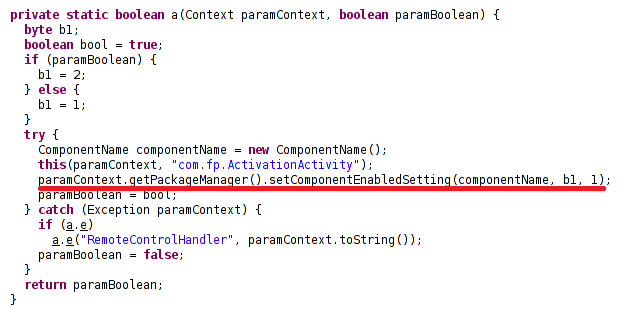
Hide SuperSU and rooting traces
Rooting an Android phone gives access to additional features and controls, but it can leave the SuperSU icon behind which might alert an individual that they are being spied on. FlexiSPY also gives the device administrator the ability to hide it as a feature.
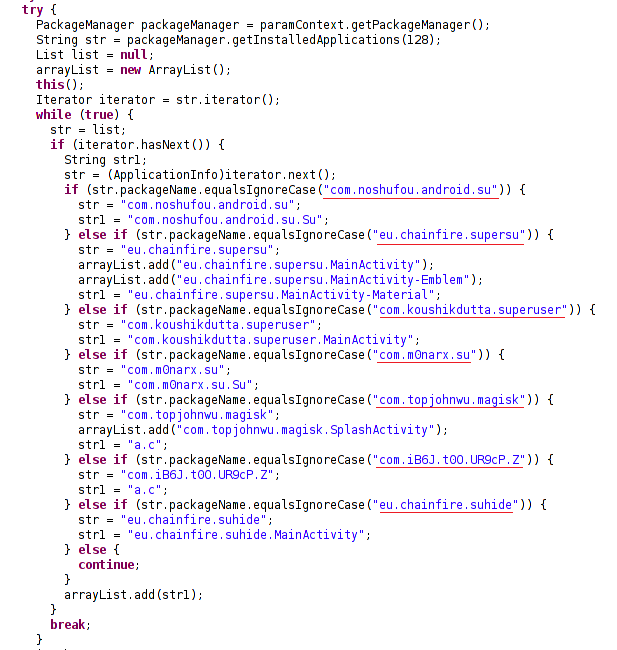
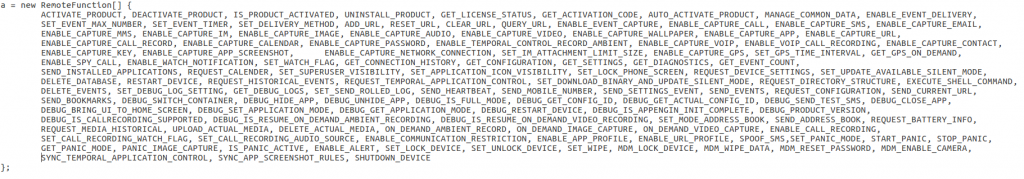
Controlling different functionalities remotely
Below is a big list of functionalities that can be turned off/on remotely through this app. In the screen shot, it can be seen that the app has a wide range of remote controlling and spying features ranging from simple recording to capturing personal information on a phone level.
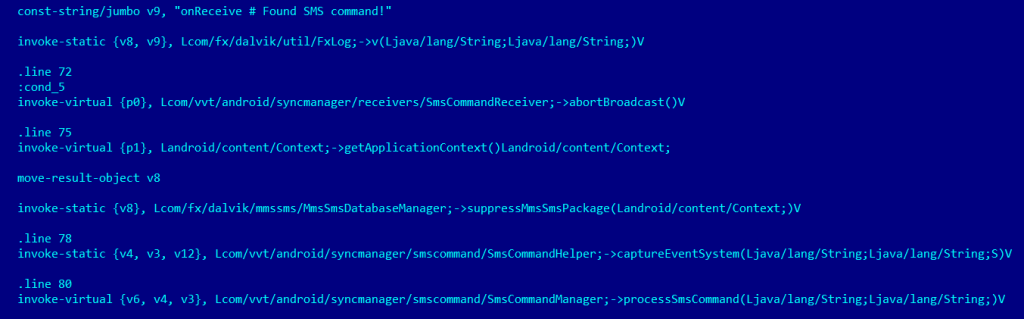
Control phone through remote SMS commands
One set of features are empowered by the ability to control the phone remotely via SMS commands. It also has the ability to hide these request and reply commands from the phone owner.



This post is also available in: German














