Securing a home network is not always easy – even if you take all the precautions you can. There are many factors that play into it and one is, of course, the router. With a good enough password and a WPA2 encryption, you were pretty much set. That is until now. Researchers have discovered a new and apparently really easy way to crack WPA/WPA2 PSK enabled Wi-Fi networks.
Discovered by accident
The new way to crack your Wi-Fi passwords was apparently discovered by accident: Security researchers working on Hashcat, a pretty popular password cracking tool, were actually trying to find new ways to crack the WPA3 wireless security protocol when stumbling upon this new WPA2 method.
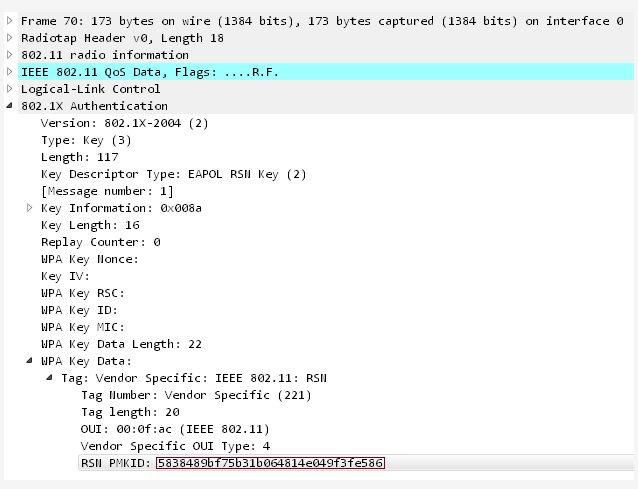
The new method could allow hackers to get the Pre-shared key (PSK) for your Wi-Fi which then, in turn, would give them access to your network. The big difference to previous methods is apparently that cybercriminals do not need to capture a full 4-way handshake. The new attack instead is performed on the RSN IE, the Robust Security Network Information Element, of a single EAPOL frame.
According to the researchers, you also don’t need a user who logs into the target network in order to capture his login data (something that was necessary before) since the attacker now communicates directly with the access point. This client-less attack brings a couple of other advantages: no more eventual invalid passwords, no lost EAPOL frames because of an access point that’s too far away from the cybercriminals, no more special output formats for the final data.
Most modern routers vulnerable
While the researchers are not sure yet for which vendors and for how many router models this technique will actually work, the outlook is not peachy: All 802.11i/p/q/r networks with roaming functions enabled could be susceptible to the new attack –and that’s most modern routers out there.
While this sounds grim there is something you can do to make sure you stay as secure as possible until WPA3, which is immune against this attack, arrives:
Use a strong password: Even with this attack, the hacker will need to brute force your password. So choose a strong Wi-Fi password, a really strong one. When in doubt you can always rely on a password manager to do the work for you.
Update your router: Update your router as soon as updates are available. If you have a really old router that does not get updates anymore, you should definitely buy a new one – at the very least once the new WPA3 routers are released.