Foreword
The Avira Threat Protection Labs has released a second global threat report for 2022, which delves into the latest threats and trends observed in Avira global telemetry during the latter half of the year. Given the diverse and complex nature of the cyber threat landscape, this research concentrates on emerging and developing cyber threats, and provides an overview based on the perspective of Avira threat researchers who continually monitor attacks worldwide. The ultimate goal of this effort is to help customers stay protected against zero-day threats and other cyber attacks.
As we enter 2023, research from the past year reveals significant activity in both the online and offline worlds. In 2022, the Avira Threat Protection Labs documented its busiest period of malware activity, with over 220 million cyber threats blocked by Avira technology in July alone; the highest recorded in over 35 years of research. The summer months also saw the emergence of various new developments and prevalent threats.
This report highlights the most important threat categories of 2022—including all types of binaries, scripts or fileless attacks on Windows, macOS and Android malware, and web threats—with a particular focus on the second half of the year. It follows on from the H1 2022 report, which was previously published and can be accessed here: https://www.avira.com/en/blog/avira-cyber-threat-report.

Global Threats Overview
Windows threats
In the second half of 2022, the cyber activity landscape on the Windows platform was dominated by coinminers, keyloggers adware, backdoor, downloader, and dropper threats. While the other threat categories remain stable, we were able to identify new variants of ransomware/banker malware.
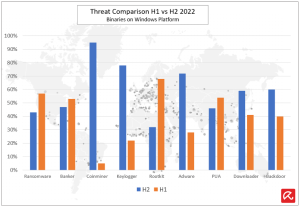
The initial chain of infection largely spread through risks like phishing email attachments, drive-by downloads, vulnerabilities, and bundled applications. Threat actors then use these initial vectors to deliver sophisticated malware, including Qakbot, Emotet, IcedID, AgentTesla, Redline stealer, etc—.. We observed that most of the ransomware samples were delivered through these sophisticated malware types and through the use of payloads from red team toolkits, such as Cobalt Strike and Brute Ratel.
We saw an increase in attacks on the Windows platform from prevalent threat families, including Qakbot, Emotet, IcedID, AgentTesla, and Redline Stealer. In 2022, some of the top variants of ransomwares were Lockbit, Azov, BianLian, Makop, Black Basta, and WannaCry.
Android threats
Adware threats ranked first among all threats detected into our telemetry in 2022, followed by potentially unwanted applications (PUAs), banker, and dropper trojans. Adware is not necessarily as dangerous as other Android threats, but it has a significant negative impact on user experience, displaying intrusive ads—sometimes even when the application is closed—to generate revenue.
We saw a net increase in adware detections and, at the same time, a decrease of more than 50% in dropper trojans in the second half of 2022. This is indicative of a general decrease in Android malware, according to Avira telemetry, showing that threat authors are focusing on adware creation instead.
We believe this shift is the result of a steady decline in outdated versions of Android operating systems installed on users’ devices: the newer the Android version, the less likely it is to get infected with malware. Android 12 version market share increased over the past year to 30.06%The number of banker Trojans also increased slightly in H2 2022 with families like Coper and Bankbot variants remaining the most prevalent.

MacOS threats
Adware was the leading macOS cyber activity in 2022 based on Avira telemetry, followed by general macOS threats (for example trojans, droppers, backdoors, information stealers etc) and rounding out with PUA.
Fortunately, in the second half of the year we saw a drastic decrease in adware detections. In general, adware is the most common type of threat on macOS. The reason for this decrease is a combination of increased security mechanisms from Apple and awareness from clients.
Still, we are seeing adware threats like “Bundlore” and “Pirrit” that are continuously present and changing their tactics to fool the users into installing them.
Even with the slight decrease in the PUA threats, however, we expect numbers will remain relatively constant throughout 2023.

Ransomware
Ransomware is a type of trojan that targets both PCs and mobile devices . Once the device gets infected, data is encrypted, and attackers start demanding money in exchange for a promised decryption key that may or may not truly exist.
Ransomware threats on Windows saw a bigturn of events in H2 2022: the shutdown of the Conti ransomware infrastructure and its rebranding to Black Basta & Black Byte, as they keep operating as Ransomware-as-a-Service (RAAS) model. Most of the ransomware types were delivered through initial vectors, including exploits, RDP, drive-by-downloads, and through other primary malware, such as Qakbot, Trickbot, Emotet, IcedID & Amadey. Some ransomware groups included red team toolkits—like Cobalt Strike, Brute Ratel—in their infection chains.
On Android, the so-called lockers are the most typical form of mobile ransomware. Also known as “screenlockers,” they lock a user’s device and block usage. This is different from traditional ransomware, which usually encrypts files.
Trends, geography, and prevalent ransomware threats
Ransomware activity increased in the first months of H2 2022 partly due to the Conti and LockBit ransomware groups. In the last months of 2022, Conti and LockBit suffered a breach and the LockBit ransomware builder and other tools were leaked. This led to the shutdown of Conti and LockBit and, consequently, a decline in ransomware activity.

The topmost attacked region by far is the US and Canada, with over a third of all registered ransomware attacks. Another big target is Brazil, which has the second highest individual share of ransomware attack events per country.

The most active ransomware variants in H2 2022 were Lockbit, Azov, BianLian, Makop, Black Basta, and WannaCry. BianLian and BlackBlasta ransomware groups aim to fill the void created by Conti ransomware.
BianLian is a GoLang-based ransomware that encrypts files and appends the “.bianlian” file extension. Black Basta uses a forged Microsoft Corporation Digital Certificate, appending the filename with a “.basta” extension, writing the ransom note named readme.txt post infection and changing the desktop wallpaper.

The ransomware cyber threats are distributed differently on the Android platform, with fewer than 10% of attacks occurring in North America. Instead, many of these attacks are in Southeast Asia, North Africa, and the Middle East. Germany, however, tops the charts, mainly due to the high user base, followed by Indonesia, Italy, and Egypt. Locker threats on Android are even more focused on Asia, with many detections occurring in India, China, and Indonesia.
The trend for H2 2022 shows us a steady number of ransom and locker campaigns going on, with prevalent families including Kloer, Rkor, Slocker, Jlocker.
Kloer and Rkor were the most common, with steady infection flow evenly distributed over the last six months, followed closely by Slocker and Jlocker locker-apps.

Bankers
We observed a steady infection from banking trojans in H2 2022, especially from Emotet, Trickbot, Qakbot, and Blackmoon families or variants. Most of these sophisticated threats spread through email attachments, LNK infectors, ISO Archive, vulnerabilities, and through drive-by downloads on the Web. These malware often team up with other threat groups to invite secondary infections, such as Cobalt Strike beacons or ransomware.
We observed that an older form of the banker “BlackMoon” is still prevalent under different variants. We investigated different techniques that were used by this malware family variants and presented our research “Techniques of a prevalent banker over the years through an offensive perspective” at theDefCamp conference in November 2022. Many banker families have different capabilities and are improving their hiding mechanisms with each new variant.
Cybercriminals target critical infrastructure. Many of these bankers have the intelligence to superimpose fake login pages over genuine banking and finance apps, with the aim of stealing the usernames and passwords that serve as banking credentials. Some use keylogging techniques or intercept multi-factor authentication (MFA) tokens or notifications, while others take advantage of Accessibility services to carry out financial fraud by impersonating the user’s actions. In addition to these methods, the latest variants of banking malware can capture screenshots, recording audio and video from infected smartphones, and creating remote sessions on affected devices. Trends, geography, and prevalent banker threats.
We observed an increase in Windows banking trojans activity in the early months of H2 2022. This was followed by a decline in the later months of the year, during which we saw a 28% decrease.

The topmost attacked country in the global Windows threat landscape is Brazil with over 33% detection events. The second most impacted country is Spain, with over 10% detection events.

Banking malware is the first and most prevalent threat in the malware category for Android, just after adware and PUA, taking up to 13% of all t cybersecurity risks. Due to their wide-ranging methods of dissemination—which include masquerading as legitimate applications like flash player updaters or Android system tools that are sometimes available on genuine Android stores, as well as being distributed via malicious SMS messages generated from an already infected device—these mobile threats are highly prevalent. The SMS messages are designed to simulate a sense of urgency, often using phishing tactics to entice the user to take immediate action, such as clicking on a link related to a missed or tracked package delivery.
The most common type of banking malware is a variant of Coper that disguises itself as utility apps like QR Code readers. Although its features are comparable to previous versions, this particular variant is unique in that it utilizes an improved detection evasion mechanism, which enables it to evade detection and be present on the Google Play store. It is labeled under package name com.qrdscannerratedx and is able to maximize its attack surface by requiring user interaction to download and install a small fake update code that installs the next stage of malware. Once installed, it cleverly poses as the Google Play Store, which can be confusing for users and may prevent them from uninstalling it.Other prevalent banker families include Bankbot spin-offs (Teabot, Sharkbot, Malibot, Exobot, Eventbot etc), and Flubot spinoffs, including the Medusa and Sova trojans.
This type of attack is most common in Germany, with Spain and France trailing. This could be due to the advanced economic state of these countries, which makes them more profitable for malware actors to attack.
Coinminers
Trojan and PUA categories were the major contributors of infection for coinminer threats, especially in the summer and autumn months. This coincides with a popularity surge of cryptocurrency platforms like Coinbase, FTX, Binance, etc. Cryptocurrencies are extremely popular as a mode of ransom for many major threat organizations , primarily because it is decentralized and unsupervised. The XMRig tool, which is widely used for cryptocurrency mining, is frequently exploited in malware infections. It is typically distributed through bundled applications, infected Windows activation hack tools such as AutoKMS, and other types of malicious droppers.
Trends, geography, and prevalent coinminer threats
We observed an increase in coinminer activity on the Windows platform in the early months of H2 2022, followed by an 11%decline in the second half.
The topmost attacked country is the United States, with over 72% detection events, and the second most impacted country is India, with over 15% detection events.

A wave of browser-mining JavaScript services that leverage site visitors’ CPU time to mine XMR (Moneros) and pays the site owners 70% of the mined value grew in popularity in H2 2022. When throttle numbers are included in an injected script, it can cause the client’s browser—which typically responds through threads—to use more CPU. Based on our research, this attack has had the greatest impact in China, with over 85% of infections occurring there. The countries with the next highest rates of infection were Ireland and Ukraine. We observed coinminer threats observed on macOS as well, with infections in 77 countries between June and November. Fortunately, there haven’t been any drastic change in the results compared to the first half of the year. European countries like Switzerland (19% of detection events), Bulgaria (13% of detection events), and Germany (12% of detection events) rank at the top.
Rootkits
A rootkit is a surreptitious software component designed to infiltrate a machine for the purpose of obtaining administrator or system-level privileges. A rootkit will conceal files, malware processes, injected modules, registry keys, user accounts, or even system registries running on system boot. Some types of rootkits are user-mode, kernel-mode, bootkits, and firmware. A rootkit can contain malicious tools that allow cybercriminals to:
- see and track everything you type on your computer.
- steal your usernames, passwords, and credit card information.
- disable the security applications you might have installed on your computer.
- alter other sensitive settings and programs in your system.
Even though the number of rootkit attacks remained constant and low compared with other threat categories in 2022, we identified a new form of rootkit, “Taohuawu,” which targets online game players in China. We investigated this cybersecurity risk and presented our research “Taohuawu, A much more sophisticated evolution from WHQL signed NetFilter rootkit” at the AVAR conference in December 2022.
Trends, geography, and prevalent rootkit threats
Rootkit attacks increased in the early months of the second half of 2022 and then gradually decreased by 4% in the remaining months.

Globally, on the Windows platform, the most attacked country is Kyrgyzstan, with over 33% detection events, followed by Nigeria, with over 31% detection events, China, with 9%, Taiwan (Republic of China), and Singapore and the US with 3% each.
The majority of rootkit infections that we have observed through our telemetry have been attributed to Netfilter and Taohuawu rootkits. These rootkits are signed using the “Microsoft Windows Hardware Compatibility Publisher” process and employ the Windows regini tool along with the command “regini c.xalm” to install the driver component.
Downloaders and droppers
Downloaders are a type of intermediary malware that is utilized in the initial stages of an infection to download the final malicious payload onto the compromised machine. In contrast, droppers are designed with the sole purpose of “installing” malware onto a target computer. When activated, a dropper may either download the malware to the targeted machine, or the malware may be stored within the dropper in a manner that prevents detection by virus scanners.
When it comes to Windows and macOS systems, it is typical for the initial stages of an infection to be executed through NonPE files. In recent months, however, the focus has shifted from Office files to script files.
Meanwhile, on Android devices, droppers are often malicious applications that carry an additional encrypted malware within their payload to avoid detection. The malicious APK is dropped, decrypted, and executed on the compromised device. If the payload is not already included in the package file, it may be downloaded via a command to the C&C server. This is typically done to bypass security vendors’ scanners, as the malicious code is not contained in the original package.
Trends, geography, and prevalent downloader and dropper threats
During the second half of 2022, we noted a rise in the prevalence of HTML files in our telemetry, surpassing other file types. Our recordings showed almost 3 million events, more than half of which involved droppers and downloaders. Among the NonPE files, Germany was the most frequently targeted country, with roughly 10.6 million attacks, half of which used HTML files. China was the second most targeted country, with around 10.4 million attacks, 30% of which used HTML files. Ireland ranked third in terms of targeted countries, with approximately 2 million attacks, the majority of which were carried out using Office documents and HTML files.
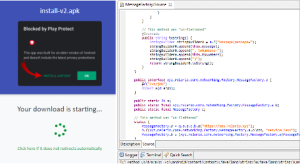
The latest trend in HTML malware involves the use of botnets to smuggle downloader and dropper files that can install malware on compromised devices. This type of attack is executed by tricking the victim into downloading an attachment file that is disguised as a password-protected PDF file or a document from Google Drive. The HTML file then downloads or drops the double- or triple-Base64 encoded bot malware onto the victim’s device. The password required to access the malicious PDF or document file is typically mentioned in the HTML file itself, as illustrated in the image below.

We also observed XLS document malware campaigns targeting the users with Qakbot downloaders. The Qakbot malware leverages an XLS file to deliver its malicious payload, with the file containing a URL that allows the DLL to be downloaded onto the target machine. Multiple URLs are employed in order to ensure the successful delivery of the payload, with alternative URLs used if one is blocked or fails. Once downloaded, the Qakbot DLL is executed using a technique known as “Hidden Files and Directories” (T1564.001), via regsvr32. The -s option is used with regsvr32.exe to install the DLL silently, without displaying any messages. The United States is the most heavily targeted country in Qakbot attacks, with Italy, the United Kingdom, and Australia following closely behind.

Keyloggers
The use of keylogger threats in attacks rose during the second half of 2022, with an increase of approximately 55% compared to the first half of the year.
During the COVID-19 pandemic, online education became more prevalent worldwide, resulting in a surge in the use of parental monitoring applications. These applications are designed to monitor children’s online and system activities, with features that include recording keystrokes, capturing desktop screenshots, monitoring web traffic and browser habits, running processes, webcam and microphone use, chat logs, and more. Some commonly used keylogger applications include Ardamax, Sprix, Refog, AllInOne Keylogger, and EMatrixSoft.
Our telemetry also revealed a notable increase in spyware threats that have the capability to capture keystrokes, steal user data and browser information, and exfiltrate the collected information without the user’s knowledge. In the second half of 2022, we detected and blocked a significant number of keyloggers, including Snake, LodaRAT (a PowerShell-based keylogger), AgentTesla, and Formbook.
Trends, geography, and prevalent keylogger threats
Keyloggers were low in the early months of H2 2022, but they rose by 44% in s the second half of 2022.

On the global Windows threat landscape, the topmost attacked country is Brazil, with over 29% detection events, and the second most impacted country is Germany, with over 20% detection events.
Adware and PUAs
The objective of “adware” applications is to show the user as many ads as possible, sometimes even when the application is closed, to generate revenue. “PUA” stands for “Potentially Unwanted Application” and includes applications that are not necessarily wanted by users, such as cleaners and fake security solutions.
Potentially Unwanted Applications (PUAs) and adware threats were seen in major attacks in the second half of 2022. They wereinstalled in bundled free software programs, droppers, and downloaders. The most prevalent adware families that caused the detection spikes in our telemetry were HiddenAd and OpenSUp. We detected most infections of Potentially Unwanted Applications with MyWebSearch, Softcnapp, Installcore, Startfenster, MediaGet, FusionCore, and OpenCandy.
Trends, geography, and prevalent adware and PUA threats
During the first few months of the second half of 2022, there was a notable increase in infections related to adware and PUAs on Windows systems. However, this trend shifted during the second half of the year, with a 9% decrease in such infections. This suggests that malware authors have begun focusing on more aggressive threats, such as coinminers, backdoors, and ransomware.

The topmost attacked country is US, with over 27% detection events, followed by China, with over 17% detection events.

On macOS, adware threats saw a slight increase in June, followed by a slight decrease in July and a normalization of infections till mid-October, when they started to increase again.

In the second half of 2022, we observed a slight increase in adware detections in nearly all countries, except for Spain, where adware decreased slightly. While the increase was less than 1%, we identified adware campaigns targeting macOS users, indicating that adware is becoming more active on this platform.
The top three countries targeted by adware were Germany, with 17.62% of total detections, followed by France with 8.36%, and Italy with 6.91% of total detections. The Pirrit adware family was the most prevalent, accounting for 78.76% of all adware detections on macOS.

While not among the top adware families in H2 2022, Bundlore is an adware family that we have frequently observed during our daily hunting. What sets Bundlore apart is that it comes in two different forms. The first and most common version is a fake “Install Flash Player” DMG application designed to trick the user into installing it. The second version is interesting from a technical perspective, as it takes the form of a shell script containing an archive or an obfuscated binary at the end. The script writes the payload to a file, unencrypts or extracts the content, and then runs the malicious payload.
The top countries targeted for macOS PUAs in the second half of 2022 were Taiwan (Republic of China), with 10.62% of detections, followed by Portugal with 7.08%, Switzerland with 4.60%, and Austria with 5.75% of detections.
Compared to the first half of 2022, only Taiwan (Republic of China) remained among the top countries targeted by Potentially Unwanted Applications, with a 3.52% increase in the number of detections. The trend suggests ongoing PUA campaigns, with prevalent families such as Blacklister, Resharer, and Speedycleaner. Jailbreak is the top PUA/OSX threat, accounting for 41.18% of all macOS PUA detections. This type of software is used to unlock, or “jailbreak,” Apple iPhones, making them more configurable but also reducing the native security offered by iOS.
Stalkerware
Stalkerware is similar to spyware and is predominantly found on mobile platforms, particularly Android. Stalkerware applications have most of the capabilities that typical spyware has, such as stealing text messages, internet-browsing data, call history, and location details.
However, stalkerware is installed intentionally by a stalker on the targeted person’s device. That means the victim is likely to know the offender, whereas spyware is typically installed by a stranger. This often occurs within toxic relationships, where one partner seeks to exert coercive control over the other. Stalkerware operates in the background, collecting sensitive information without alerting the victim, making it difficult to detect and remove from the device.
While some individuals have written articles to raise awareness about stalkerware, there are unfortunately those who have promoted its use. In response, Google has announced new measures and policies aimed at preventing stalkerware applications from being published on their Play Store over the last year. They also introduced the isMonitoringTool flag, which can help identify legitimate monitoring apps.
Trends, geography, and prevalent stalkerware threats
Stalkerware detections increased by almost 75% in H2 2022 when compared to H1 2022. These detections were observed across 94 countries, with Singapore having the highest percentage of detections at 17.9%, followed by the US and Italy at 16.3% and 14.1%, respectively. At Avira, stalkerware applications are detected using the prefix PUA/Stalk.
SMS Trojans
On Android, SMS trojans are still ranked in the top five most widespread threat types, accounting for more than 5% of infections in H2 2022.
The top three most prevalent SMS trojans families in H2 were: SMS Agent (38% of infections), followed by SMS Reg (13% of infections), and SMS forwarder (8% of infections).
SMSAgent is the name we use as a catch-all for our SMS Spyware families, and it currently ranks #1 on our prevalent list. One of the novel aspects of this spyware is that there are many repacked apps from Google Play that use improved obfuscation techniques and new packers such as NP manager.
SMSReg is a Premium SMS Trojan which silently registers the victim to non-free services. It ranked #2 on our prevalence list for H2 2022, following the steady numbers we observed in H1.
The most recent threat we observed is SMSFactory, which differs from previous campaigns by scheduling SMS messages to premium numbers for persistence, rather than creating premium subscriptions. It uses older Android API levels to circumvent the latest privacy protections and instructs users to click the “Install Anyway” button.
The SMS Forwarders family ranks #3 on our prevalence list and includes several types of apps that intercept incoming SMS messages and forward them to the attacker. In Q2, we observed a slight change in exfiltration channels, with some threats starting to use alternate channels, such as FTP, to avoid detection. Trends, geography, and prevalent SMS trojans
SMS Trojans were a persistent threat, with variants including Roaming Mantis, SMS Factory, FormBook, TeaBot, and Joker, along with generic SMS Thief malware. However, there were only been a few spikes in July and October. We do not anticipate a significant increase in this type of threat in the near future.
Our data also indicates that the top three countries affected by SMS Trojans are Germany, Iran, and the US, with very few threats detected outside of these countries.
The most prevalent SMS trojan threat is SMSReg, with the highest number of detections in Iran, and it is often found through ads or on market sites such as jhoobin.com. The next most common threats are various types of spyware, typically found in Germany and the US. Simple SMS forwarders come in last place and are easy to create by copying code from different GitHub projects and modifying it, which is why they are so widespread.
Phishing and other web threats
In 2022, the amount of malicious web threats and phishing attacks showed some fluctuation. In the middle of May, they were almost equal in volume, but then there was a decrease in the number of malware URLs and an increase in the number of phishing attacks in the second half of the year.

Phishing target industries
Phishing attacks are a major threat to both businesses and consumers, serving as the primary method for various cyberattacks. A single phishing email can cause a company to fall victim to ransomware or for a user to inadvertently reveal company email account credentials that can be utilized in further attacks against customers by a malicious actor. The financial sector has been the most targeted industry due to its critical infrastructure, accounting for 30% of global phishing threats. Hackers frequently impersonate banks like Sparkasse or Chase to acquire users’ credentials and financial information.
The logistics/shipping industry is the second most targeted sector, with 16% of global phishing threats, followed by ecommerce/retail with 14%.


Geographic distribution of phishing URLs
In H2 2022, the country with the highest number of phishing attacks was the United States, with over 61% of detection events. The second most targeted country was Germany, with over 13% of detection events.

Exploit kits by network activity
In the second half of 2022, we observed an increase in the number of attacks using the Styx exploit kit compared to previous months, making it the most prevalent exploit kit. Styx redirects users to a malicious landing page that hosts exploit files, targeting various vulnerabilities. The redirector link may arrive via email as part of a spam campaign.
We also saw a slight increase in the activity of the RedKit exploit kit, while Pony—which was one of the most prevalent exploit kits in H1 2022—decreased in the second half of 2022.

Files dropped by URLs
PDF files were the dominant type of malicious file hosted by URLs in 2022, as they were one of the preferred file types for malware authors in phishing attacks. While there was an increase in the number of PDF files observed in H1 2022, there was a 22% decrease in attacks in H2 2022.
However, the number of URLs hosting malicious PE and ELF files increased in H2 2022. Among the most prevalent PE payloads hosted and delivered via download from URLs was Asbit, an emerging remote desktop trojan. Asbit uses various methods to bypass endpoint and network detection, such as the use of DNS over HTTPS (DoH) to resolve the IP addresses of its control servers, allowing it to get past network DNS filters.

Vulnerabilities and exploits
Payload generation tools and frameworks are commonly used in the wild to gain and maintain access to a remote computer, utilizing multiple exploitation modules. Our telemetry shows a 3300% increase in the number of samples generated in this context in H2 2022 compared to H1. The chart below ranks the most commonly used frameworks in 2022, with Metasploit being one of the most popular and integrated into other organizations in the top, such as TheFatRat and Veil. The number of samples generated using these frameworks is increasing month by month, with the most prevalent payloads attempting to obtain a reverse shell or communicate with a command-and-control server. Notably, the Sliver organization has seen a significant increase in sample size, as this relatively new framework has gained more attention in recent months.

Common and prevalent exploits and newly discovered vulnerabilities
In the first half of the year, we observed active exploitation of several vulnerabilities affecting popular software such as Microsoft Office Suite (Follina CVE-2022-30190) and Spring Framework (CVE-2022-22965 Spring4Shell).. As the year continued, the number of samples identified in the wild decreased. However, there are still active reports of exploitation attempts on potentially outdated and vulnerable systems.
ProxyNotShell is a type of attack that targets Microsoft Exchange Server, similar to its predecessor, ProxyShell. This attack involves multiple chained vulnerabilities that can result in Remote Code Execution. The vulnerabilities were reported during Microsoft Patch Tuesday in September 2022, and a Proof-of-Concept code was later released in the following months. The delay in the release of the PoC code allowed more time for system updates and limited the number of active follow-up attacks.
Throughout 2022, the IoT segment experienced a significant number of publicly disclosed vulnerabilities with full exploits available in the wild. These vulnerabilities impacted various devices, including routers, NAS systems, and mobile phones. This heightened activity was linked to the Pwn2Own 2022 contest, which disclosed several zero-day vulnerabilities affecting a wide range of IoT devices.
Threat actors are still exploiting the ZeroLogon (CVE-2020-1472) vulnerability, which affects unprotected and outdated machines. This vulnerability is related to the cryptographic process during the login flow, allowing attackers to connect with the AD Netlogon remote protocol and authenticate using NT Lan Manager (NTLM).
In addition, the PetitPotam (CVE-2021-36942) vulnerability was active in the second half of the year. It affects Windows servers that have the AD certificate service (ADCS) configured without protection against NTLM relay attacks at the AD level.
Outro and predictions
Avira Telemetry data suggests that the prevalent cyberthreat families, such as Qakbot, Trickbot, Emotet, AgentTesla, and IcedID, will likely continue to be active in the first half of 2023 and beyond. While ransomware and banker trojans are slightly declining compared to H1 2022, they still remain a part of the current cyberthreat landscape and may become more prevalent in the future.
New variants of ransomware are expected to emerge, utilizing various delivery approaches and tactics. Coinminer and keylogger threats showed a massive increase in activity during the second half of 2022. The trend of most common malware families shifting toward script files like HTML and PDF is expected to continue and possibly intensify. Downloaders and droppers in HTML are anticipated to deliver various payload variations through various campaigns.
In the second half of 2022, we witnessed severe cases of Remote Code Execution (RCE) and other attacks in the vulnerabilities landscape, and we predict that outdated devices will continue to be targeted in the future. Threat actors will continue to use exploitation and penetration testing frameworks to gain access to the targeted systems and generate payloads. We anticipate that Metasploit will remain the most commonly used payload generation framework, but we also expect to see an increase in the usage of new frameworks by organizations.
Adware will continue to be the dominant threat for mac0s, with malware families such as Pirrit, while PUAs like coinminer, keylogger, and “jailbreak” applications are expected to increase in activity in the first half of 2023 and beyond.
Additionally, we can also expect an increase in SMS trojan attacks, with threat actors using different types of malware to intercept and forward SMS messages, register users to non-free services, and steal sensitive information. The financial sector will continue to be the primary target for phishing attacks, with threat actors impersonating banks and financial institutions to harvest user credentials and financial data. In the IoT segment, publicly disclosed vulnerabilities with full exploits available in the wild will continue to pose a threat to a wide range of devices, ranging from routers to NAS systems and mobile phones. Finally, we predict that the usage of script files such as HTML and PDF will continue to intensify, with downloaders and droppers delivering various payload variations through different campaigns
In the second half of 2022, there was an increase in the use of URLs to host phishing pages, as compared to the distribution of malware files via URLs. However, the use of HTML attachments in malicious emails to deliver phishing URLs remains a prevalent trend. We anticipate that this trend will continue to target industries such as finance and logistics in the first half of 2023.