It only takes two steps to circumvent Apple’s Gatekeeper controls and add malware directly to a Mac. This strategy enables a hacker to place malware on any Mac where they have direct remote access — and may potentially be exploited via a script.
This bypass of Apple’s own controls, as demonstrated below on a Mac running High Sierra 10.13.6 with Gatekeeper version 181.1, shows the risks from relying solely on the “I have macOS, so I don’t need to worry about malware” approach. Here is the analysis from Avira’s Bogdan Anghelache.
A brief intro to Apple’s Gatekeeper
First, let’s talk about “Gatekeeper”, Apple’s built-in security solution. Gatekeeper makes sure that you can run only valid applications. An application is valid if it is signed by a certificate issued by Apple or it has a valid Developer ID signature (the latter means that the developer of the said application is not a fake one and that Apple gave him the “green light”). Any application that doesn’t meet the above criteria will be blocked, which means that you cannot run it (you can, of course, disable this check). Please note that Gatekeeper comes in action only when a user wants to run an application by double clicking on it. If he/she wants to run it from the terminal, Gatekeeper won’t come in action (this allows a hacker to run the said application programmatically, through a script).
Building on the discoveries of AV-Comparatives
Do all of the above mean that you can’t run an application if it’s “invalid”? Well, the answer to that is no. There is a way to run such applications and implicitly bypass Gatekeeper, which I’ll show below. The “good” part is that you don’t have to be a macOS savant to do that.
The Avira lab got the hint from researchers of AV-Comparatives, Andreas Clementi, Stefan Haselwanter, and Peter Stelzhammer, who reported the issue to Apple in March 2019. Apple recognized their discovery and released a security update for macOS Mojave in mid-May 2019. Since they found this vulnerability on macOS Mojave 10.14.4, we decided to test it on macOS High Sierra 10.13.6.
Following the chain of command
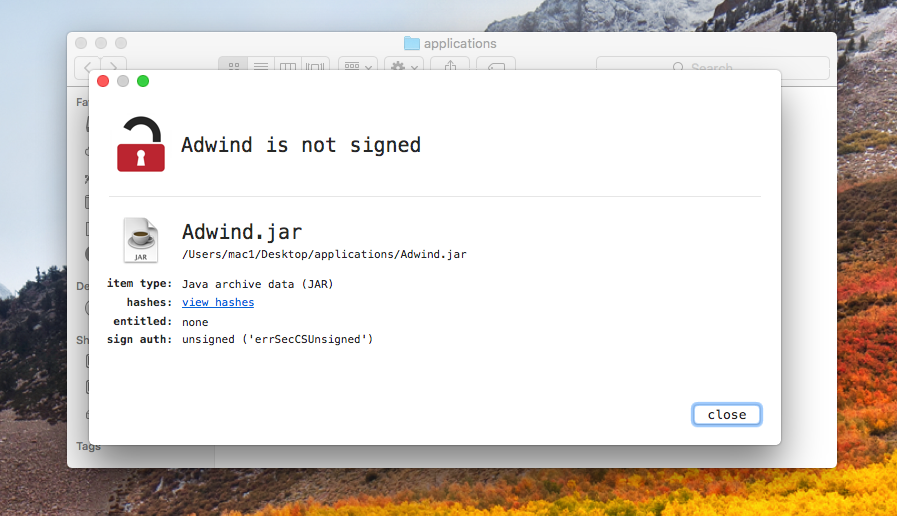
In the “applications” folder, I downloaded a java piece of malware from the “Adwind” family.
As shown below, the application is not signed, which means it’s not valid to run.
Picture 3
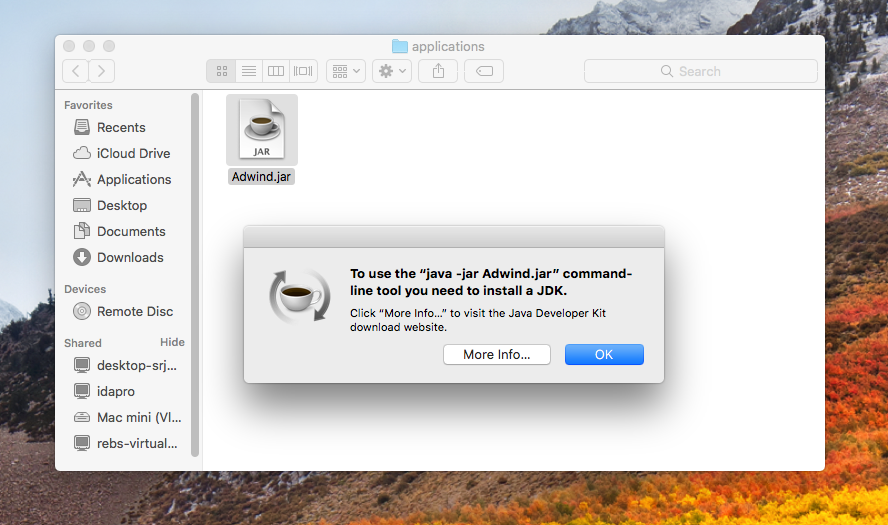
This is the warning message from Gatekeeper, when I try to run it.

Picture 4
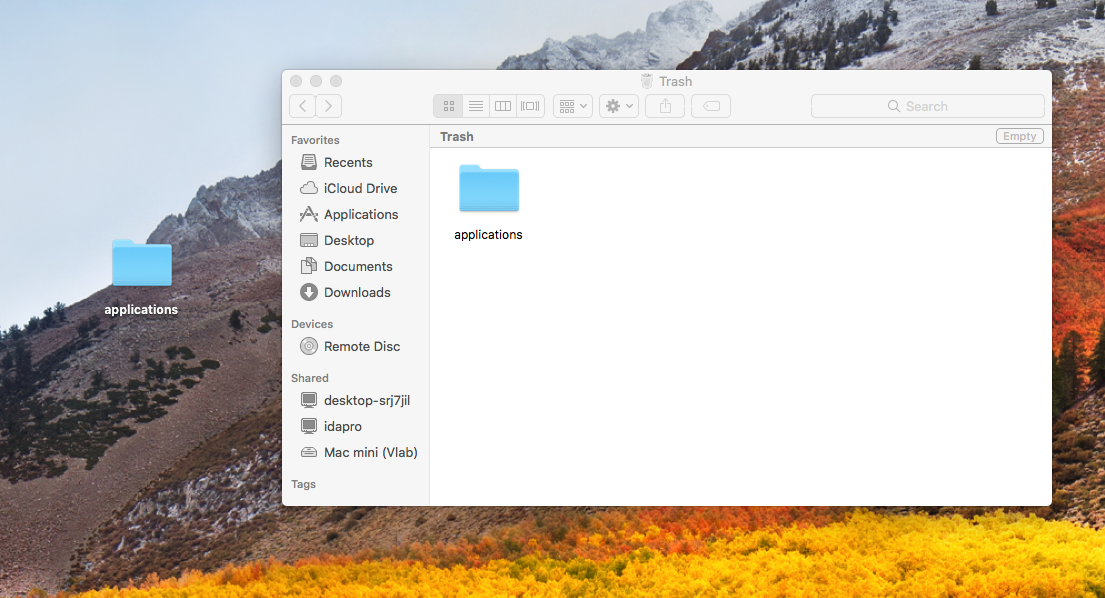
To bypass this, I just deleted the folder, created a new one with the same name and replaced it with the original folder that contains the malware.
After that, I was able to run “Adwind.jar” without any problems. As you can see, no warning from Gatekeeper popped up.
On top of AV-Comparative’s team findings, the Avira lab discovered that this exploit doesn’t rely on deleting the folder containing the invalid application, so I found another way to do it. I renamed the original folder as “applications copy”, created an empty one with the same name as the original one (“applications”) and just copied over the content (still, the “replace” method was used, but this shows that you don’t have to delete the original folder).
Again, I was able to run the piece of malware without any problems.
Conclusion:
It seems that this vulnerability is not patched on macOS High Sierra 10.13.6, so we recommend that you use a third-party anti-virus product such as Avira Security for Mac. Also, the exploit has been tested in macOS Catalina 10.15 without any results, which means the bug has been patched in this version, so we recommend upgrading your macOS to the latest version.
We also recommend that Apple patch this vulnerability in macOS High Sierra.