Our 2020 threat summary reflects an unprecedented year in so many ways. The global threat environment was visibly affected, with cyber criminals making COVID-19 a central part of their phishing campaigns. Windows malware remained predominant, while the number of threats targeting all platforms increased every month. In this article, we’ll summarise what was seen by Avira’s Protection Labs through 2020, but if you are interested in the detail, then take a look at our Q4 and 2020 detailed threat review.
2020 global summary and comparison with 2019
In 2020, we saw a surge in targeted malware threats. Compared with 2019, the volume of threats we identified – and prevented – worldwide increased by about 15%. The biggest changes occurred at the beginning and end of the year, apparently correlating to periods of lockdown.
Let’s take a closer look at the types of attacks that Avira blocked in 2020. Our data covers all platforms (Windows, macOS and Android) and highlights countries users and devices targeted by malicious activity (specifically, we measure attacks per user).
Countries in darker red saw the highest attack rates. The lighter the color, the less malware detected. Bear in mind that this is a summary chart. Each OS, each type of malware, will have a different distribution (which we cover in our Q4 and 2020 detailed threat review).

Only August 2020 showed significantly lower attack volume than the same time the previous year. April saw a significant peak of activity, and then we’ve observed strong growth in attacks through the last four months.

Over the past few years, Avira has seen more unique malware threats than ever. The telemetry we receive from our sensor network, and the data we collect each day from our partners, is added to our threat intelligence data-lake and used to train our threat models.
Our threat intelligence database has grown from 556 million threats in 2019 to around 652 million at the end of 2020. This means approximately 17% of all threats ever observed have emerged in the last 12 months. Although this doesn’t tell us precisely how many threats are found in the wild, it clearly shows that malware authors are producing an almost endless stream of malware.

What happened in….Q1 2020
The descent into a global pandemic created a platform for malspam (malicious spam) and phishing as bad actors adapted their campaigns to take advantage of the disruption. Our Q1 report focussed on the growth of phishing and malspam campaigns. It also highlighted a surge in Emotet related attacks, which global law enforcement agencies finally started to get control of in January 2021. Read more about Q1 2020.
In early 2020, our Vulnerability Detection Team, part of Avira’s Protection Labs, highlighted the top 5 vulnerabilities they considered to be of greatest concern. The vulnerabilities opened a wide range of operating systems to exploit. Windows, iOS and Android, it did not matter; unpatched systems were open to attack. These vulnerabilities make our first vulnerability report list based on our assessment of their criticality, coverage, and impact.
What happened in….Q2 2020
As employees started to work-from-home, traditional cyber-security architectures began to come under pressure. The transition away from the traditional perimeter security model accelerated as millions of employees connected remotely through corporate VPNs. VPNs were a technology that some had been about to call ‘end-of-life’ – not anymore. We saw malware authors shift from volume-based attacks to more complex and sophisticated attack methodologies, attacking VPN vulnerabilities and leveraging MS Office and script-based threats. Consumers were also widely targeted with malware. Attacks ranged from spyware and adware to more sophisticated banking trojans and SMS stealers. These were often distributed under the flag of COVID-19 related apps. Read more in our Q2 report.
What happened in….Q3 2020
Q3 2020 saw a significant rise – nearly 50% – in the number of traditional malware, exploit based threats, and coin miner attacks. However, adware/PUA, mobile, and script-based threats saw a decline compared to the previous quarter. The surge in general malware attacks was of particular concern; this category contains the most dangerous threats found in the wild. Read more.
Our mid-2020 vulnerability report looked at some of the most critical vulnerabilities open to exploit. This report saw multiple critical high-risk vulnerabilities disclosed (and patched) across a wide range of software platforms. The most critical of these vulnerabilities was “Zerologon” which impacted domain controllers. Around the same time, Microsoft identified the SIGRed vulnerability within their DNS mechanism.
What happened in….Q4 2020
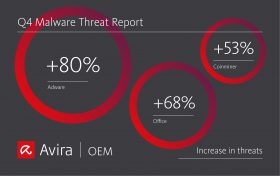
It was almost red across the board in the last quarter of 2020. Overall threat detections for Q4 surged by 47%. Adware nearly doubled over the previous quarter. Office, script and coinminer malware increased by more than 50% compared to the previous quarter. Read more.
Evolution of threats in the world (forecast 2021)
No one can predict the future with certainty, especially when you know how adaptive, creative and quick malware authors can be. But we’ll have a go at forecasting how threats will evolve around the world in 2021.
One of the big challenges will likely be a shift away from ‘traditional’ PE malware (Windows executables) towards attacks using non-PE files (documents etc) and fileless attacks.
Every year, the number of vulnerabilities detected in common applications breaks records. The software we use is more complex and the world is more connected than ever – a boon for vulnerability hunters looking to exploit them. Obviously, not all vulnerability hunters are malware authors, but we believe more vulnerabilities will be exploited in 2021.
The world of threats is also evolving at an organizational level. Malware-as-a-service (MaaS) enables hackers to use tools and malware created by other authors. Often the service comes with surprisingly good support. Although many tend to use the terms “hackers” and “malware authors” synonymously, the rise of MaaS means they are not. Of course, we would expect some groups (and occasionally government agencies) to keep their creations to themselves and only use them for highly targeted attacks against high priority objects.
Assuming someone does not hack them and steal their creation.
Whether you are an existing technology partner, thinking about licensing one of our solutions, or just interested in malware research, we hope you will find something of interest.













Want to comment on this post?
We encourage you to share your thoughts on your favorite social platform.